Author: Denis Avetisyan
A new approach combines graph neural networks and manifold learning to visualize and interpret the complex behavior of Internet of Things devices.
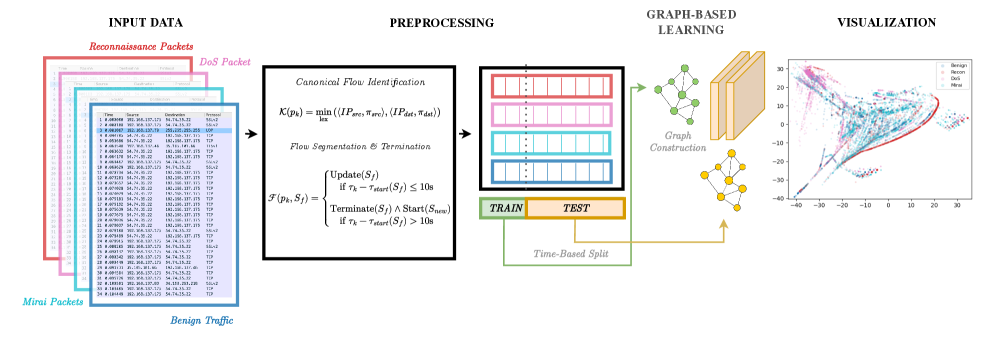
This research introduces a framework for creating interpretable embeddings of IoT network traffic, enabling improved intrusion detection and network behavior analysis through feature attribution and topological insights.
The increasing complexity of Internet of Things (IoT) networks presents a paradox: while generating valuable data, their dynamic topologies challenge traditional security monitoring approaches. This is addressed in ‘Interpreting Manifolds and Graph Neural Embeddings from Internet of Things Traffic Flows’, which introduces a novel framework leveraging Graph Neural Networks and Manifold Learning to generate interpretable, low-dimensional embeddings of network traffic. The resulting visualizations enable both accurate intrusion detection-achieving an F1-score of 0.830-and insightful analysis of evolving network states, highlighting phenomena like concept drift. Could this approach ultimately bridge the gap between complex machine learning and actionable intelligence for network administrators and security professionals?
The Expanding Threat Landscape: Network Security at a Crossroads
Conventional network intrusion detection systems, designed for simpler network environments, now face a critical challenge: the escalating complexity and volume of modern data streams. These systems often rely on signature-based detection, matching known attack patterns, which proves ineffective against novel threats and encrypted traffic. The sheer scale of data generated by contemporary networks-fueled by cloud computing, mobile devices, and the proliferation of applications-overwhelms these systems, leading to high rates of false positives and, crucially, missed genuine intrusions. Consequently, organizations are increasingly vulnerable as traditional methods struggle to differentiate between legitimate activity and malicious intent, necessitating a shift towards more intelligent, adaptable security solutions capable of analyzing network behavior in real-time and identifying anomalies that indicate potential threats.
The proliferation of Internet of Things (IoT) devices has dramatically broadened the potential entry points for malicious actors, creating a vastly expanded attack surface. Unlike traditional computers with relatively robust security measures, many IoT devices – from smart refrigerators to security cameras – are often manufactured with minimal security considerations due to cost constraints and rapid production cycles. This leaves them vulnerable to compromise, and when compromised, they can be co-opted into large-scale botnets. The 2016 Mirai botnet, for instance, famously leveraged hundreds of thousands of insecure IoT devices to launch massive Distributed Denial of Service (DDoS) attacks, disrupting major internet services by overwhelming them with traffic. The sheer scale and distributed nature of these botnets, fueled by the ever-growing number of connected devices, present a significant and evolving challenge to network security, demanding innovative approaches to detection and mitigation.
The escalating prevalence of Distributed Denial of Service (DDoS) attacks presents a growing threat to online availability and digital infrastructure. These attacks, once relatively simple floods of traffic, have evolved into multi-vector assaults leveraging compromised devices – often within expansive Internet of Things networks – to overwhelm target systems with a diverse range of malicious requests. Modern DDoS attacks frequently combine volumetric attacks, aiming to saturate bandwidth, with application-layer attacks that target specific vulnerabilities in web servers and applications, making them harder to mitigate through traditional methods. The increasing sophistication includes the use of reflection and amplification techniques, where attackers exploit legitimate services to multiply the volume of malicious traffic, and the deployment of ‘botnets’ comprised of millions of compromised devices, allowing for attacks of unprecedented scale and duration, ultimately disrupting critical services and causing significant financial losses.
Modeling Network Complexity: The Power of Graph Neural Networks
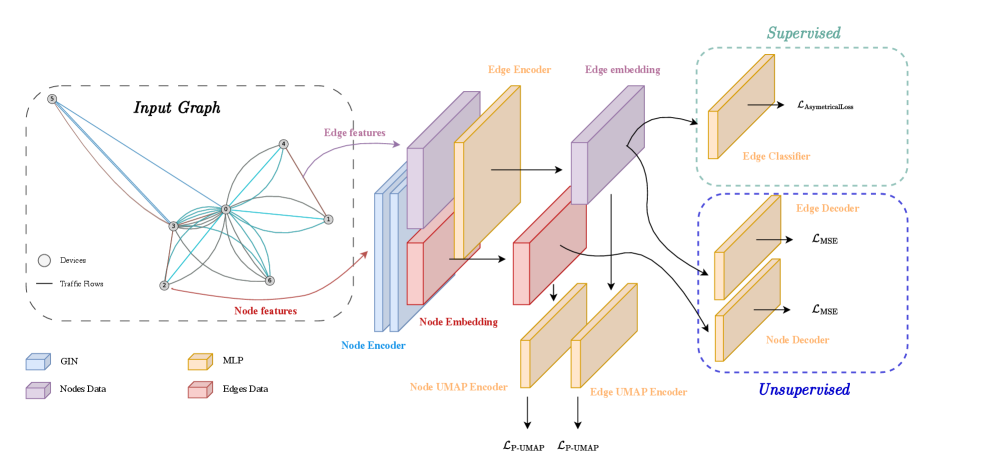
Graph Neural Networks (GNNs) facilitate network traffic analysis by modeling network data as a graph structure. In this representation, network entities – such as hosts, switches, or individual flows – are defined as nodes, and the relationships between them – like communication paths or data transfer – are represented as edges. This allows GNNs to move beyond traditional analysis methods that treat network data as isolated events, instead leveraging the inherent relational information. By encoding network topology and traffic patterns into the graph structure, GNNs can learn complex dependencies and patterns, enabling tasks such as anomaly detection, traffic prediction, and security threat identification. The graph structure allows the application of graph convolution and message passing algorithms to aggregate information from neighboring nodes, effectively capturing the contextual information vital for accurate network analysis.
The efficacy of Graph Neural Networks (GNNs) is directly correlated to the characteristics of the network topology being analyzed. GNN performance is impacted by factors such as network density, degree distribution, clustering coefficient, and the presence of community structure. Specifically, highly clustered networks can facilitate more effective message passing between nodes, improving learning. Conversely, sparse or disconnected networks may limit the flow of information and require adjustments to the GNN architecture or training process. The scale of the network – the number of nodes and edges – also significantly impacts computational cost and memory requirements, necessitating scalable GNN implementations for large-scale network analysis. Furthermore, the presence of specific topological features, like bottlenecks or critical nodes, can influence the GNN’s ability to accurately model network behavior and detect anomalies.
Network traffic can be represented as a graph using different approaches, each emphasizing distinct behavioral characteristics. Flow-Centric Graphs model each network flow as a node, with edges representing relationships like shared source/destination pairs or similar statistical features. Host-Centric Graphs, conversely, represent network hosts as nodes and connections as edges representing communication links, providing a view of the network’s infrastructure. Temporal Graphs extend these representations by incorporating time as a dimension, tracking changes in network structure and flow characteristics over specific intervals; this is achieved by creating multiple graph instances, each representing the network state at a given time, or by adding timestamps to edges and nodes. The selection of graph representation depends on the specific network analysis task, with each approach offering unique insights into network performance, security, and anomalies.
Illuminating the Black Box: Interpretable Security Through Attribution
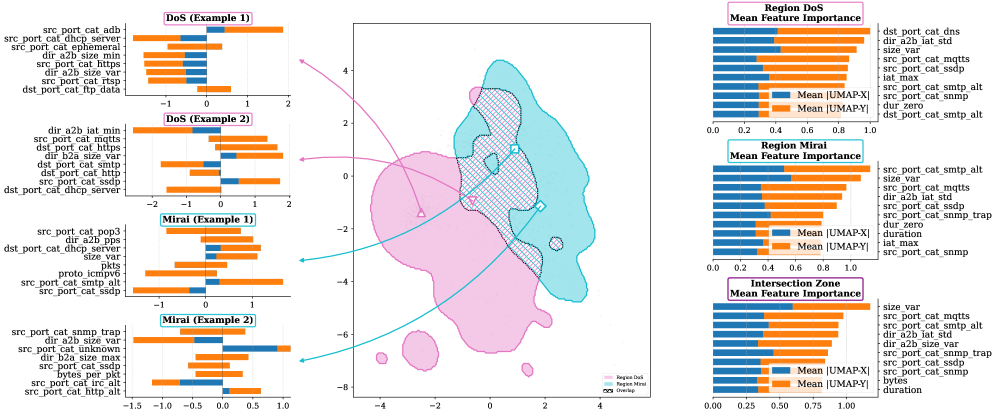
Feature attribution techniques, notably Shapley Additive Explanations (SHAP), quantify the contribution of each input feature to a Graph Neural Network’s (GNN) output for intrusion detection. SHAP values are calculated by averaging the marginal contribution of each feature across all possible feature combinations, providing a consistent and theoretically sound method for feature importance assessment. In the context of network traffic analysis, this allows security analysts to determine which specific network features – such as packet size, inter-arrival time, or port number – most strongly influenced the GNN’s classification of a traffic sample as malicious or benign. The resulting feature attributions can be used to validate the GNN’s decision-making process, identify potential biases, and pinpoint the characteristics of detected attacks.
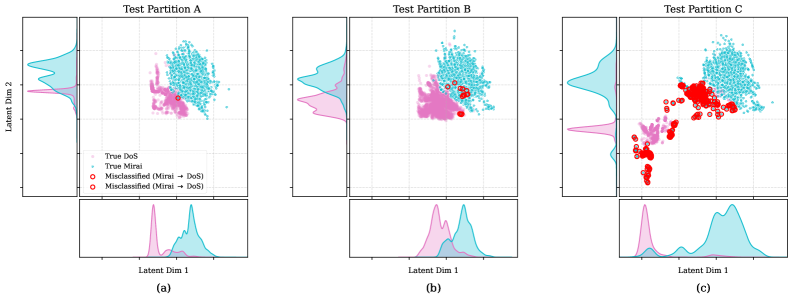
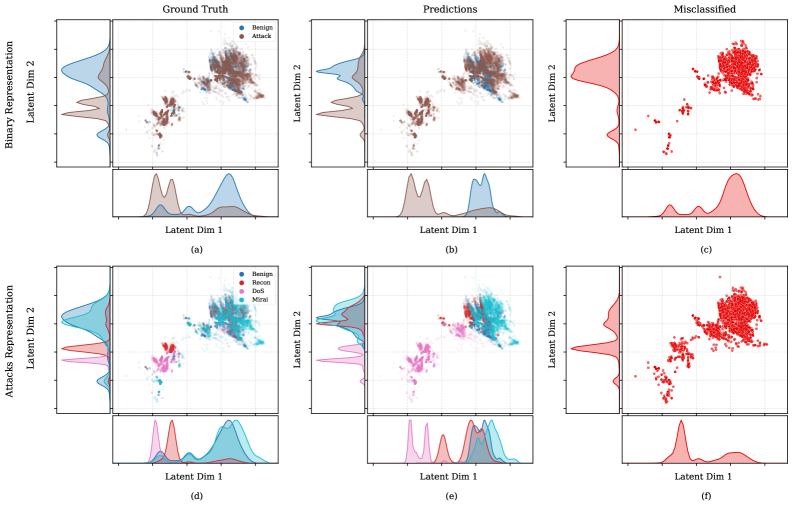
Manifold learning techniques, particularly Parametric Uniform Manifold Approximation and Projection (PUMAP), address the high dimensionality inherent in Graph Neural Network (GNN) embeddings. GNNs often generate embedding vectors with hundreds or thousands of dimensions, making direct interpretation and visualization difficult. PUMAP operates under the assumption that these high-dimensional embeddings lie on a lower-dimensional manifold. It projects the data onto this manifold while preserving local neighborhood relationships, effectively reducing dimensionality to two or three dimensions for visualization purposes. This reduction allows security analysts to observe clustering patterns in the embeddings, potentially revealing groupings of similar network traffic characteristics or distinct attack types that might not be apparent in the original high-dimensional space. The resulting visualizations can then be used to identify anomalies and understand the underlying structure of the network data as represented by the GNN.
The application of interpretability techniques directly supports security analyst workflows by enabling validation of Graph Neural Network (GNN) predictions. Analysts can assess whether the features driving a GNN’s classification align with known attack characteristics, reducing confidence in potentially incorrect classifications. This validation process is critical for identifying false positives – instances where legitimate network traffic is incorrectly flagged as malicious – which require manual investigation and consume valuable security resources. Furthermore, by understanding the feature contributions leading to a prediction, analysts can gain deeper insights into previously unknown or evolving attack vectors, informing threat intelligence and improving overall security posture.
Demonstrating Efficacy: Performance and the Challenge of Concept Drift
The performance of the Graph Neural Network (GNN) in discerning malicious network activity isn’t solely judged by its ability to classify traffic, but also by the quality of its clustering – its capacity to group similar traffic patterns together. Quantifying this clustering quality relies on metrics like the Davies-Bouldin Index and Silhouette Score; lower Davies-Bouldin Index values and higher Silhouette Scores indicate better clustering. Results demonstrate the GNN achieves a Davies-Bouldin Index of 4.227 for edges and 4.381 for nodes, representing a significant improvement over baseline models that analyze raw network data. Simultaneously, the GNN exhibits a Silhouette Score of 0.142 for edges and 0.111 for nodes, further validating its ability to create distinct and well-separated clusters of network traffic, potentially highlighting previously unseen patterns or anomalies that would be obscured in simpler analyses.
The implemented Graph Neural Network pipeline exhibits substantial efficacy in network intrusion detection, as evidenced by a binary F1-Score of 0.830. This metric signifies a strong balance between precision and recall in accurately identifying malicious traffic, indicating the system minimizes both false positives – incorrectly flagging benign activity as harmful – and false negatives – failing to detect genuine threats. Achieving this score demonstrates the GNN’s capability to effectively learn complex patterns within network data and generalize to unseen traffic, representing a significant advancement over traditional intrusion detection methodologies reliant on static signatures or simpler analytical techniques. The high F1-Score suggests the model reliably distinguishes between normal network behavior and malicious activity, offering a robust foundation for proactive network security measures.
Effective network intrusion detection necessitates a dual classification approach. Systems aren’t simply tasked with labeling traffic as either malicious or benign – a binary distinction – but also with pinpointing the specific type of attack underway. This multiclass classification is crucial for targeted response and mitigation; identifying a denial-of-service attack, for instance, requires a different strategy than addressing a phishing attempt or a malware infection. Consequently, intrusion detection systems must be engineered to simultaneously excel at both broad categorization and fine-grained identification, demanding sophisticated algorithms and comprehensive datasets capable of representing the full spectrum of network threats.
The proposed network security system exhibits enhanced ability to group similar network behaviors, as evidenced by improvements in clustering quality metrics. Specifically, the system achieves a Silhouette Score of 0.142 for edge analysis and 0.111 for node analysis; these values represent a demonstrable increase when contrasted against baseline results utilizing raw, unanalyzed network data. A higher Silhouette Score indicates more distinct and well-separated clusters, meaning the system more effectively identifies and categorizes different types of network traffic – a critical step in isolating potentially malicious activity. This improved clustering not only aids in accurate intrusion detection, but also allows for a more nuanced understanding of network dynamics and facilitates proactive security measures.
Network Intrusion Detection Systems face a fundamental challenge: the ever-shifting landscape of network traffic, a phenomenon known as Concept Drift. These systems are not designed to operate in static environments; instead, the patterns that define malicious activity constantly evolve as attackers refine their techniques and network usage changes over time. Consequently, a system that performs effectively today may quickly become obsolete as new attack vectors emerge or legitimate network behavior shifts. Addressing this requires continuous adaptation, typically through ongoing retraining of the detection models with the latest network data. This iterative process allows the system to learn and adjust to the evolving characteristics of both benign and malicious traffic, ensuring sustained accuracy and resilience against emerging threats. Without this continuous learning cycle, the efficacy of even the most sophisticated intrusion detection system will inevitably degrade, leaving the network vulnerable to undetected attacks.
The pursuit of understanding complex systems, as demonstrated by this framework merging Graph Neural Networks and Manifold Learning, echoes a fundamental principle of efficient design. It strips away superfluous detail to reveal underlying structure. This research doesn’t merely detect intrusions within IoT traffic; it aims to visually articulate the network’s topology, offering a clear representation of behavior. As Alan Turing observed, “Sometimes people who are unkind are unkind because they are unkind to themselves.” The same applies to complex systems – often, obscuring the core structure stems from internal complexities rather than inherent difficulty. This work exemplifies how clarity, achieved through careful reduction and insightful visualization, is paramount to effective interpretation and, ultimately, robust security.
What Remains to be Seen
The pursuit of intelligibility in complex systems invariably reveals the limits of the tools employed. This work offers a path toward interpreting the latent space of IoT network traffic, yet the very act of embedding – of reducing dimensionality – necessarily discards information. The question is not whether perfect reconstruction is possible, but whether the remaining representation captures sufficient signal to warrant its abstraction. Future investigations must address the trade-off between fidelity and interpretability with greater precision, perhaps by incorporating mechanisms for quantifying lost information or explicitly modeling uncertainty.
Current approaches to feature attribution, while useful, remain largely post-hoc. A more elegant solution would involve architectures inherently capable of self-explanation, where the embedding process itself is transparent. This demands a re-evaluation of prevailing network designs, moving beyond opaque, layered structures toward models that prioritize causal clarity. The challenge lies not in discovering more complex representations, but in simplifying existing ones without sacrificing predictive power.
Ultimately, the true measure of this work, and similar endeavors, will not be the accuracy of intrusion detection, but the capacity to reveal fundamental truths about network behavior. The goal should not be to simply identify anomalies, but to understand why they occur, and to anticipate them before they manifest. Such understanding requires a shift in perspective – from viewing networks as systems to be secured, to viewing them as complex organisms to be understood.
Original article: https://arxiv.org/pdf/2602.05817.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- The Batman 2 Villain Update Backs Up DC Movie Rumor
- Adolescence’s Co-Creator Is Making A Lord Of The Flies Show. Everything We Know About The Book-To-Screen Adaptation
- Exodus Looks To Fill The Space-Opera RPG Void Left By Mass Effect
- New survival game in the Forest series will take us to a sci-fi setting. The first trailer promises a great challenge
- Zombieland 3’s Intended Release Window Revealed By OG Director
- Future Assassin’s Creed Games Could Have Multiple Protagonists, Says AC Shadows Dev
- The Best Battlefield REDSEC Controller Settings
- First Glance: “Wake Up Dead Man: A Knives Out Mystery”
- My Favorite Coen Brothers Movie Is Probably Their Most Overlooked, And It’s The Only One That Has Won The Palme d’Or!
- ‘Stranger Things’ Actor Gives Health Update After Private Cancer Battle
2026-02-06 23:30