- Cthulhu Stealer attacks Mac devices and steals credentials from a long list of crypto wallets.
- Malware aimed at draining funds from crypto wallets installed on Macs is rising.
As a seasoned researcher with a decade of experience in cybersecurity, I’ve seen my fair share of malware threats targeting various platforms. However, it seems that Mac devices are becoming increasingly popular targets for cybercriminals, with the latest addition being the Cthulhu Stealer.
A recently discovered malware named Cthulhu Stealer is on the rise, specifically targeting devices running MacOS in order to pilfer crypto wallet information. This makes it one more example of malware posing a threat to Mac users. Cado Security has uncovered this new threat and released a report explaining how it captures wallet data. This revelation follows close on the heels of reports detailing another harmful program, AMOS, interfering with the Ledger Live software application for Mac.
For quite some time, there’s been a common understanding in the cultural zeitgeist that MacOS systems are impervious to malware. However, while MacOS is known for its security, instances of MacOS malware have been increasingly detected in recent years.
Cthulhu Stealer disguises itself as legitimate software for MacOS, operating as an Apple Disk Image (DMG). When users open the malware application, it prompts them for their password. When they follow through, it prompts them for their MetaMask password. It then stores the sensitive wallet details in text files on their devices. The malware can also do the same for other wallets, including Atomic, Trust, Binance, Coinbase, and numerous others. It gathers other information, too, like users’ IP addresses, OS versions, hardware and software details, and more.
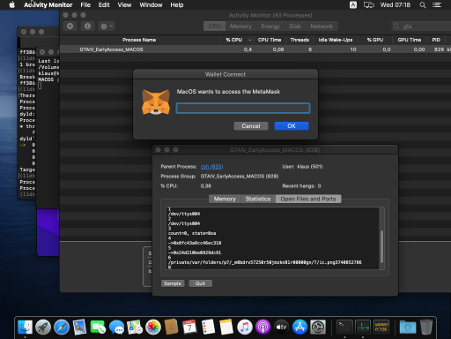
Cthulhu Stealer prompting MetaMask password. Source: Cado Security
According to Cado’s explanation, the primary purpose of Cthulhu Stealer is to swipe login credentials and digital wallet information from various platforms, including gaming accounts. In his report, he points out that Cthulhu Stealer shares similarities with another malware designed for MacOS called Atomic Stealer. The cybersecurity team suspects that Cthulhu Stealer might be a modified variant of Atomic Stealer.
The Rise of Malware-as-a-Service Offerings
Cthulhu is being sold as a Malware-as-a-Service (MaaS) product for a subscription fee of $500 every month, with subscription-based malware services growing in demand. The main developer also takes a significant portion of every exploit, paying those deploying the malware a percentage of their earnings. Cado’s investigation found that “Cthulhu stealer sold on two well-known malware marketplaces which are used for communication, arbitration and advertising of the stealer, along with Telegram.”
On the other hand, there could potentially be issues arising within the malware deployment process for its users. Several individuals have expressed concerns because the creator is reportedly running an exit scam, failing to distribute the promised shares of the unlawful profits.
Read More
- UFO PREDICTION. UFO cryptocurrency
- Finding Resources in Palworld: Tips from the Community
- AAVE PREDICTION. AAVE cryptocurrency
- The Last Epoch Dilemma: Confronting the Gold Dupe Crisis
- BONE PREDICTION. BONE cryptocurrency
- Celebrating Hu Tao’s Birthday in Genshin Impact
- Skull and Bones: Gamers’ Frustrations with Ubisoft’s Premium Content Delivery
- Michelle Yeoh Will Not Appear in ‘Avatar 3,’ Says James Cameron: ‘She’s in 4 and 5’
- DF PREDICTION. DF cryptocurrency
- Abiotic Factor: Players Discuss the Need for Quick Character Adjustments in-game
2024-08-27 15:43