
As a seasoned crypto investor who has witnessed countless data breaches and their devastating aftermaths, I can confidently say that centralized data networks are a ticking time bomb waiting to go off. My personal experience with these systems being compromised multiple times has left me with a deep-rooted skepticism towards them.
The billions of dollars spent annually on cybersecurity measures seem like a drop in the ocean compared to the $10 trillion in damages caused by data breaches in 2024 alone. The list of high-profile victims, from AT&T to the U.S. Office of Personnel Management, serves as a stark reminder that no one is immune to these attacks.
Recent advancements in AI have only magnified this issue, as these valuable models require access to sensitive user data to function effectively. However, the traditional cloud model cannot provide the necessary security and privacy guarantees required for such applications. Apple’s announcement of Apple Intelligence this year highlighted these issues, emphasizing the need for a new approach.
Fortunately, Web3 cloud platforms like Super Protocol offer a promising solution in the form of Blockchain-Orchestrated Confidential Cloud (BOCC) networks. These systems, built on confidential hardware and governed by smart contracts, address all of Apple’s concerns while providing superior privacy and security without sacrificing performance or latency.
In the spirit of transparency and humor, I must admit that as an investor, I find it amusing how these massive corporations keep promising better security measures, only to be outwitted by clever hackers time and again. But with BOCCs on the rise, perhaps we’ll finally see a shift towards more secure digital infrastructure—one where my personal data remains just that: personal!
Decentralized data networks, controlled by a single entity, have had structural vulnerabilities for many years. The reason? They are susceptible to single points of failure. If only one entity (or even several) has access to a database, then there is just one weak spot that, when compromised, grants full control. This poses a significant risk for networks storing sensitive data such as customer information, government documents, and financial records, as well as those managing critical infrastructure like power grids.
2024 saw a staggering number of digital records being illegally obtained, resulting in an approximate loss of $10 trillion! Prominent instances of these breaches involve almost all customer information and call logs from AT&T, approximately half of the personal health data from U.S. citizens, 700 million user records belonging to companies utilizing Snowflake, 10 billion distinct passwords held by RockYou24, and Social Security details for a massive 300 million Americans.
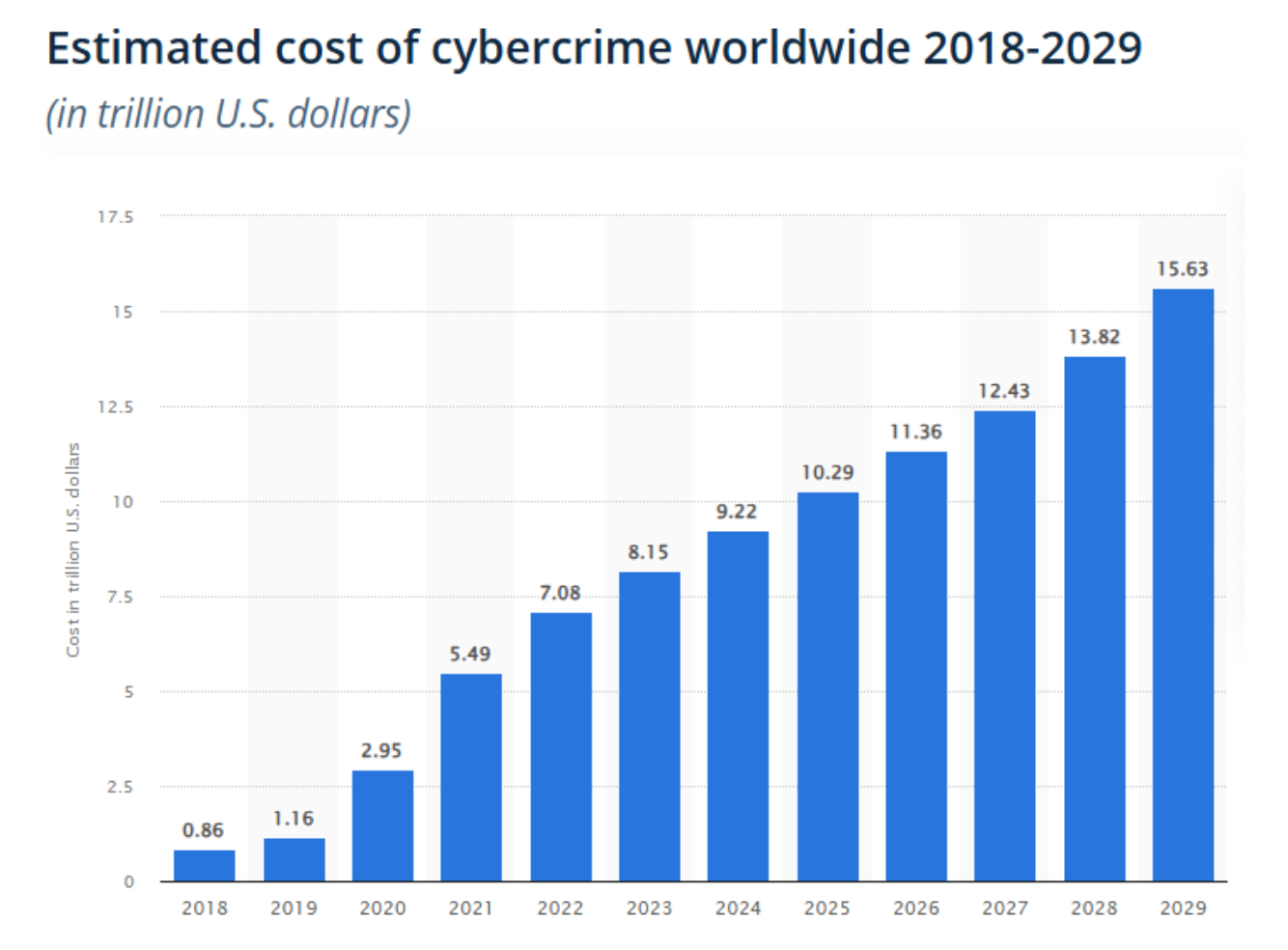
It’s important to understand that the vulnerability of centralized networks isn’t limited to just the private sector; even governments and critical national infrastructure are affected. Recent examples of breaches include the theft of records from 22 million Americans at the U.S. Office of Personnel Management, leaked sensitive communications from various U.S. federal agencies, compromised biometric data for 1.1 billion Indian citizens, and ongoing Chinese intrusions into several American internet service providers.
It’s not only businesses that have to worry about cybersecurity; centralized systems used by governments and essential services are also at risk, as demonstrated by various high-profile breaches around the world.
Despite the massive financial investments made annually in cybersecurity, data breaches are escalating both in size and frequency. It’s evident now that minor improvements won’t suffice to address these security loopholes; a fundamental overhaul of our network structure is needed instead.
AI magnifies the issue
In simpler terms, as technology progresses in creating intelligent AI systems that can automate daily tasks and boost work efficiency, it’s crucial to remember that the most effective AI applications demand context, which often involves handling confidential details such as health, financial, and personal information. However, due to the high computational power these models need, they cannot typically run on common devices like computers or smartphones and instead rely on vast public cloud networks, such as AWS, to manage intricate inference requests. Unfortunately, the challenges associated with securely linking sensitive user data with cloud-based AI have emerged as a major obstacle for widespread adoption, given the security concerns related to centralized systems.
As a forward-thinking crypto investor, I’ve noticed that even tech giants like Apple are acknowledging the limitations of the traditional cloud model. In their announcement for Apple Intelligence earlier this year, they emphasized the necessity of utilizing larger, more intricate models in the cloud. This shift towards advanced, cloud-based solutions is becoming increasingly crucial as the old model seems to be losing its viability.
They name three specific reasons:
- Privacy and security verification: Providers’ claims, like not logging user data, often lack transparency and enforcement. Service updates or infrastructure troubleshooting can inadvertently log sensitive data.
- Runtime lacks transparency: Providers rarely disclose software details, and users cannot verify if the service runs unmodified or detect changes, even with open-source tools.
- Single point of failure: Administrators require high-level access for maintenance, risking accidental data exposure or abuse by attackers targeting these privileged interfaces.
Fortunately, Web3 cloud platforms offer the perfect solution.
Blockchain-Orchestrated Confidential Cloud (BOCC)
BOCC networks, unlike AWS, are constructed entirely using confidential hardware and overseen by smart contracts. Despite being in its infancy, this infrastructure has been under development for years and is now beginning to welcome Web3 projects and traditional Web2 enterprise clients. A notable demonstration of this architecture is Super Protocol, a cloud platform designed for enterprises that operates entirely via on-chain smart contracts and is built within trustless execution environments (TEEs). These secure hardware enclaves ensure that both code and data remain verifiably confidential and secure.
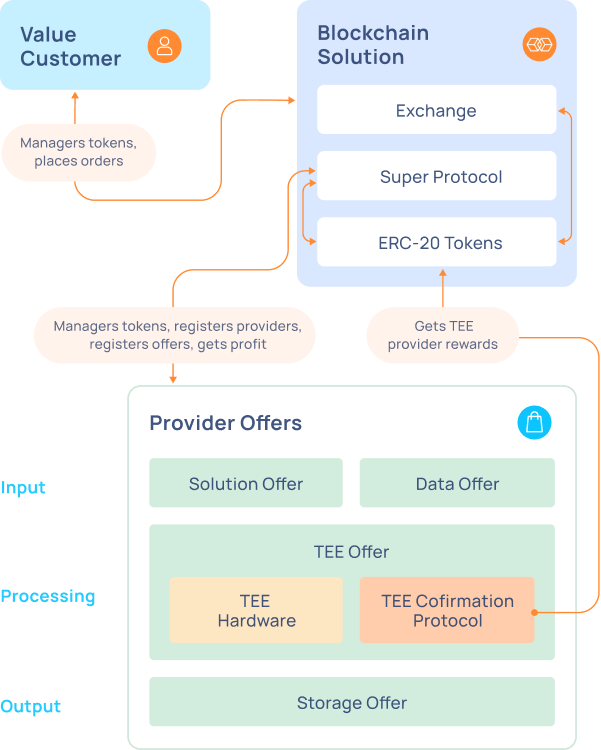
The implications of this technology address all of Apple’s concerns noted earlier:
- Privacy and security verification: With public smart contracts orchestrating the network, users can verify whether user data was transported and used as promised.
- Workload and program transparency: The network also verifies the work done within the confidential TEEs, cryptographically proving the correct hardware, data, and software were used, and that the output wasn’t tampered with. This information is also submitted on-chain for all to audit.
- Single point of failure: Network resources (data, software, hardware) are only accessible by the owner’s private key. Therefore, even if one user is compromised, only that user’s resources are at risk.
As a researcher delving into the realm of Web3, I’m excited about the potential for cloud AI to bring about disruptive change. However, it’s crucial not to overlook the value of Blockchain Organizational and Collaborative Consortia (BOCCs) in the context of centralized data networks like power grids, digital voting systems, military IT, and more.
BOCCs can be strategically implemented to enhance privacy, security, and verification, all while maintaining optimal performance and minimizing latency. In a time when our digital infrastructure is increasingly vulnerable, BOCCs offer a promising solution that bolsters its resilience. Essentially, we’re talking about leveraging blockchain-orchestrated systems to strengthen and safeguard our digital world.
As a seasoned journalist with a keen interest in the world of cryptocurrency, I have witnessed the rapid growth and evolution of this innovative industry over the past few years. In my role at CoinDesk, I have had the opportunity to interview experts, attend conferences, and delve deep into the technical aspects of blockchain technology. However, it is important to note that the opinions expressed in this piece are solely mine and do not necessarily reflect those of CoinDesk, Inc., its owners, or affiliates. In this column, I will share my personal insights on the current state of cryptocurrency and offer my perspective on the future trends and challenges facing this dynamic sector.
Read More
- SUI PREDICTION. SUI cryptocurrency
- „People who loved Dishonored and Prey are going to feel very at home.” Arkane veteran sparks appetite for new, untitled RPG
- LDO PREDICTION. LDO cryptocurrency
- Destiny 2: A Closer Look at the Proposed In-Game Mailbox System
- Clash Royale Deck Discussion: Strategies and Sentiments from the Community
- Jennifer Love Hewitt Made a Christmas Movie to Help Process Her Grief
- ICP PREDICTION. ICP cryptocurrency
- Naughty Dog’s Intergalactic Was Inspired By Akira And Cowboy Bebop
- Critics Share Concerns Over Suicide Squad’s DLC Choices: Joker, Lawless, and Mrs. Freeze
- EUR IDR PREDICTION
2025-01-01 20:57