Author: Denis Avetisyan
A new wave of integrated sensing, communication, and machine learning technologies promises to overcome the unique challenges of safety, security, and efficiency in modern mining operations.
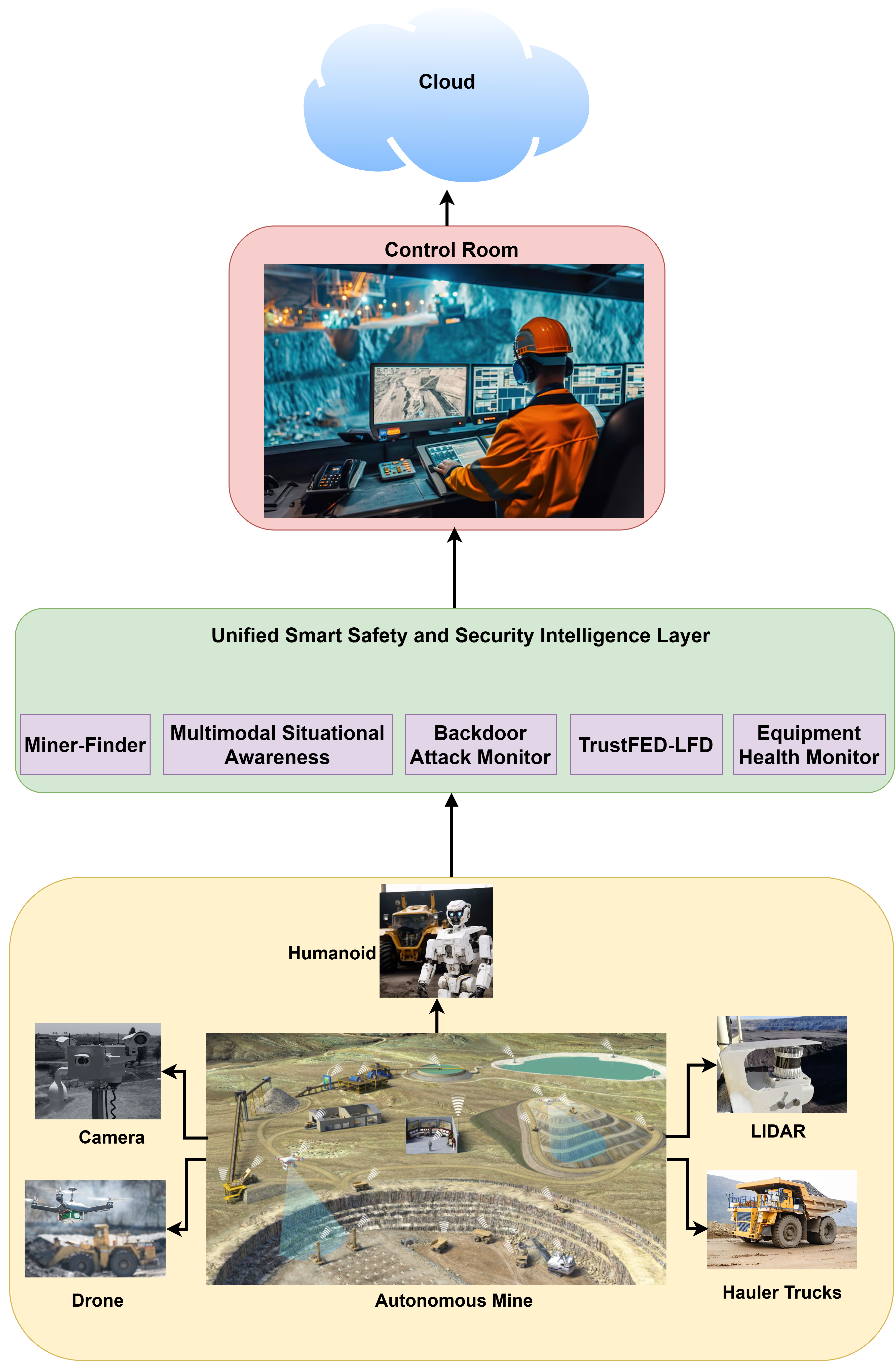
This review proposes a unified architecture leveraging Delay-Tolerant Networking, Federated Learning, and multimodal perception to address connectivity limitations, enhance situational awareness, and mitigate adversarial threats in autonomous mining environments.
Despite advances in automation, underground mining remains a uniquely challenging environment due to poor connectivity, limited perception, and emerging cyber threats. This paper, ‘Future Mining: Learning for Safety and Security’, proposes a unified architecture integrating multimodal sensing, secure federated learning, and resilient communication to address these limitations. The resulting framework enhances miner localization, hazard understanding, and predictive maintenance while mitigating risks from compromised sensors or malicious attacks. Can this integrated approach pave the way for truly autonomous and trustworthy intelligent mining systems capable of operating reliably under even the most adverse conditions?
The Imperative of Subterranean Perception
Conventional perception systems, typically reliant on well-lit and structured scenes, falter significantly when deployed in the chaotic environments of underground mines. Standard segmentation models, designed to differentiate objects based on visual cues, are hampered by pervasive darkness, necessitating increased reliance on noisy sensor data. The complex geometry of mine tunnels – irregular walls, haphazardly placed equipment, and constantly shifting piles of material – creates visual ambiguity that overwhelms these algorithms. Furthermore, the dynamic nature of mining operations – moving vehicles, operating machinery, and personnel traversing the space – introduces temporal inconsistencies that challenge the ability of static models to accurately interpret the surroundings. This combination of factors results in decreased accuracy, increased false positives, and ultimately, a compromised ability to perceive the subterranean landscape effectively.
Inaccurate hazard detection and diminished situational awareness within underground mines present substantial safety risks to both human workers and increasingly prevalent autonomous vehicles. The inherent darkness, coupled with dynamic environments – shifting materials, moving machinery, and unpredictable geological features – frequently overwhelms conventional perception systems. This can lead to delayed identification of critical dangers such as unstable rock formations, exposed electrical wiring, or the presence of personnel in hazardous zones. Consequently, personnel face increased risks of collisions, entrapment, or exposure to dangerous conditions, while autonomous vehicles may navigate incorrectly, potentially causing damage, disruptions, or even escalating safety concerns within the confined and complex subterranean spaces.
The demands of modern mine operations necessitate perception systems far exceeding the capabilities of conventional technologies. A truly robust system must reliably interpret sensor data within the uniquely challenging underground environment-characterized by low lighting, dust, complex geometry, and constant movement of equipment and personnel. This isn’t merely about identifying obstacles; it requires nuanced understanding of the scene to differentiate between static infrastructure, dynamic hazards, and navigable pathways. Consequently, the development of such a system directly impacts operational efficiency, minimizes the risk of accidents, and enables the safe deployment of increasingly autonomous robotic solutions crucial for future mining endeavors. Without dependable perception, optimizing productivity and ensuring worker safety remain significant, ongoing challenges.
A Unified Architecture for Subterranean Safety
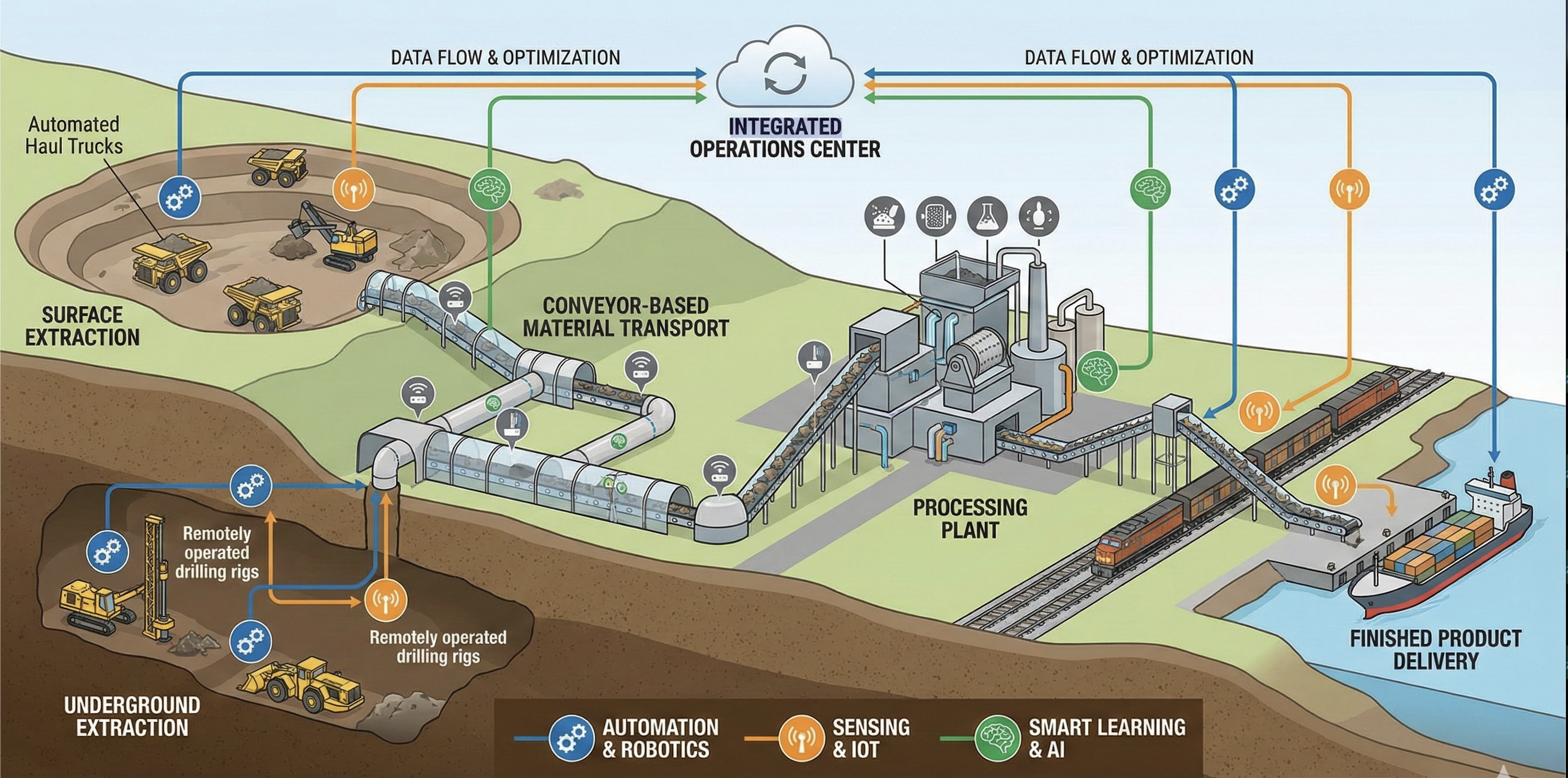
The Unified Smart Safety and Security Architecture for mining operations functions by integrating four core components: sensing, perception, communication, and decision-making. Sensing utilizes a network of deployed hardware – including gas detectors, proximity sensors, and vibration monitors – to collect real-time data regarding the mine environment and equipment status. This raw data is then processed by the perception layer, which employs algorithms to identify patterns, anomalies, and potential hazards. Secure and reliable communication networks transmit this processed information to a central control system. Finally, the decision-making component leverages this synthesized data to automate safety protocols, alert personnel to risks, and optimize operational efficiency, ultimately increasing the resilience of the mining operation against unforeseen events.
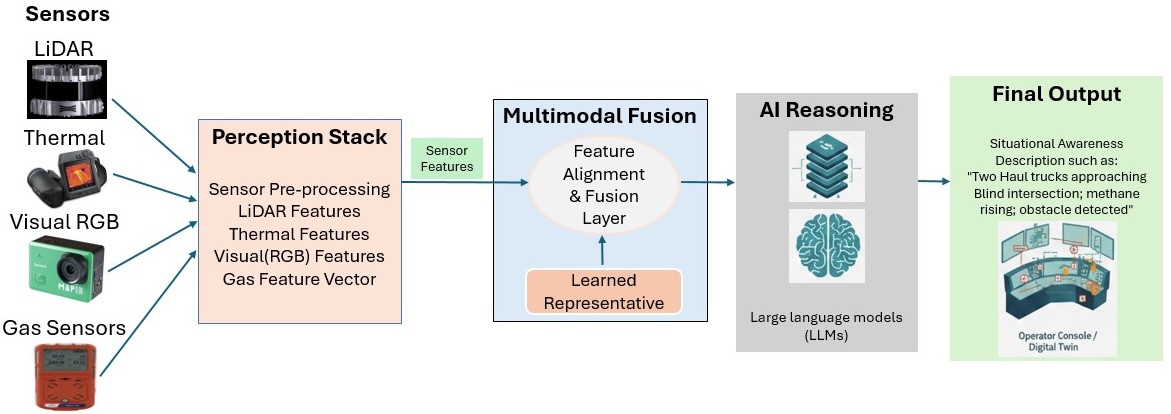
The Multimodal Situational Awareness Module functions as the core analytical component within the Unified Smart Safety and Security Architecture. It achieves enhanced environmental understanding by employing data fusion techniques, integrating information streams from diverse sensor types – including LiDAR, radar, cameras, gas detectors, and personnel tracking systems. This integration isn’t simply data aggregation; the module applies algorithms to correlate and validate data, reducing false positives and increasing the reliability of environmental models. The resulting composite data provides a holistic and dynamic representation of the mine’s conditions, enabling improved hazard detection, proactive risk management, and informed decision-making regarding operational safety and efficiency.
The Digital Mine Twin functions as a dynamic virtual replica of the physical mine environment, integrating real-time data from sensors, equipment, and personnel. This allows for the creation of detailed simulations used for both retrospective data analysis and predictive modeling of potential scenarios. Specifically, the twin facilitates the testing of operational changes, optimization of resource allocation, and proactive identification of safety hazards before they manifest in the physical mine. Data fusion within the twin enables the validation of sensor data, correction of inaccuracies, and the creation of a consistently updated baseline for predictive algorithms, improving the reliability of decision-making processes.
Precise Localization in Disconnected Environments
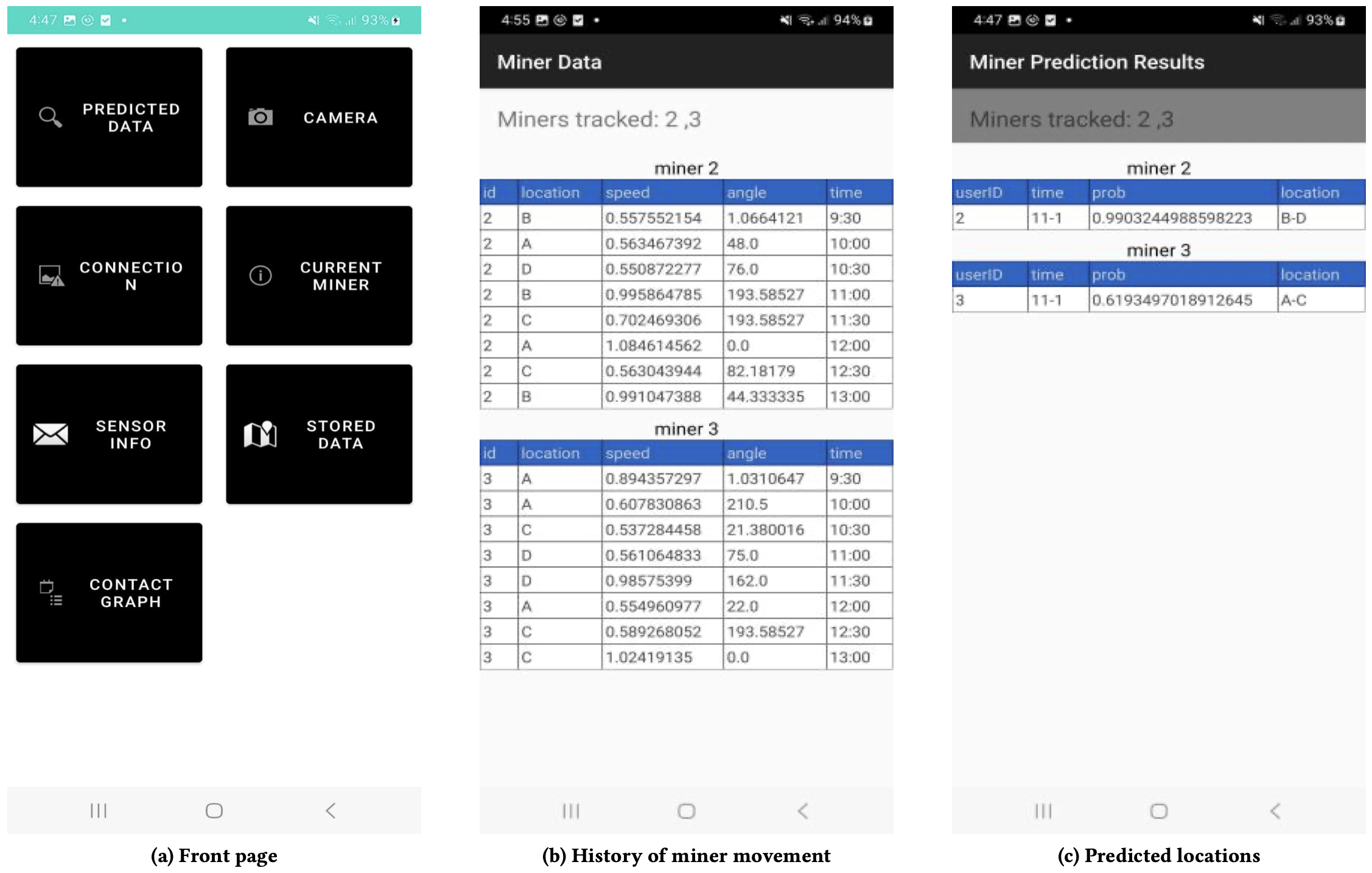
The Miner-Finder Module is designed to provide continuous miner location data despite communication disruptions common in underground mining environments. Traditional localization systems relying on constant network connectivity are ineffective where radio signals are blocked or intermittent. This module operates by maintaining location estimates even during periods of complete communication loss, utilizing predictive algorithms and stored map data to extrapolate probable miner positions. The system prioritizes resilience to network outages, ensuring safety and operational awareness are maintained regardless of communication infrastructure status. This is achieved through onboard processing and a distributed architecture that minimizes reliance on external communication for core functionality.
The Miner-Finder module utilizes a Graph Autoencoder Long Short-Term Memory (GAE-LSTM) Predictor to estimate miner locations by analyzing historical movement data and generating predicted trajectories. This prediction is then integrated with Contact Graph Routing (CGR), which leverages a dynamically constructed communication graph representing potential miner contact opportunities. CGR facilitates location estimation even with intermittent connectivity by routing location updates through intermediate miners, effectively extending the range of localization beyond direct communication.
System accuracy is directly correlated with the performance of both the GAE-LSTM predictor and the Contact Graph Routing (CGR) protocol. The GAE-LSTM predictor’s ability to accurately forecast miner movement – based on historical data and observed patterns – minimizes localization error when communication is lost. Simultaneously, CGR’s adaptive routing capabilities ensure messages are delivered efficiently even with intermittent connectivity or node failures; the protocol dynamically adjusts routes based on network conditions and node availability. Degradation in either the prediction accuracy of the GAE-LSTM or the responsiveness of CGR will result in increased localization error and reduced system reliability.
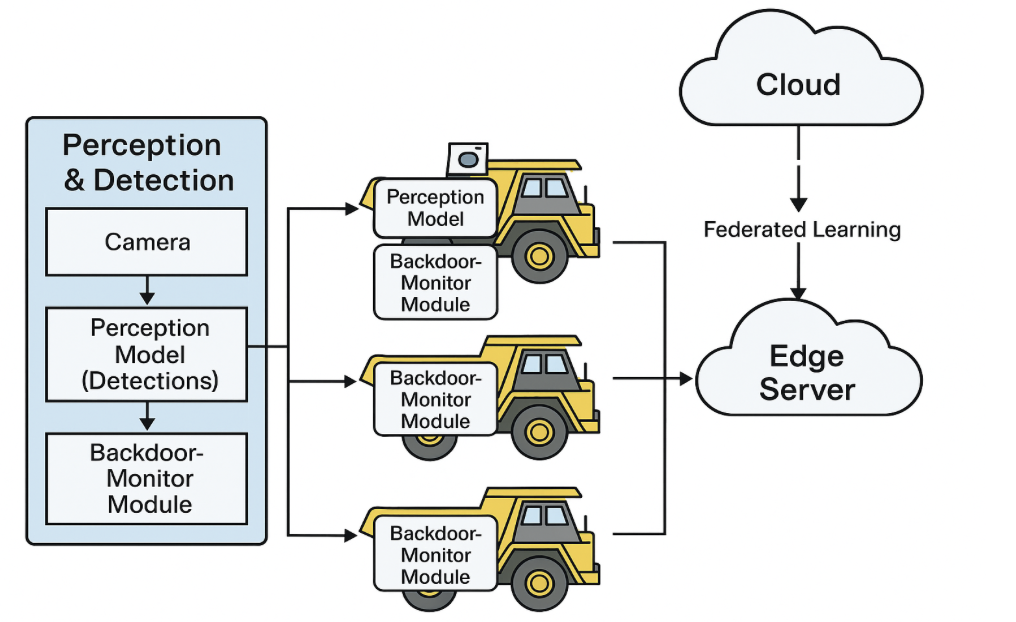
Fortifying the System Against Malicious Interference
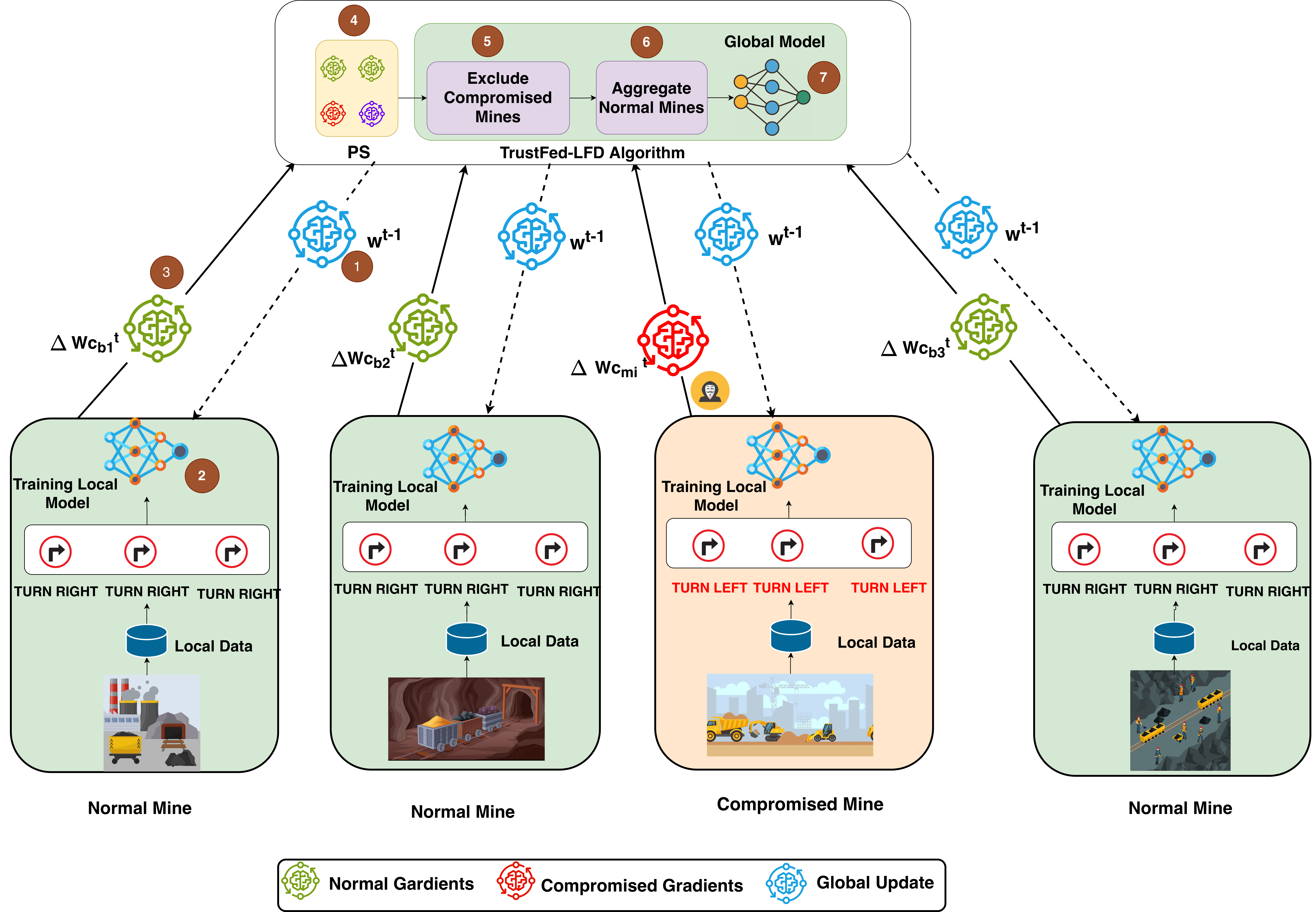
The foundational reliability of any safety-critical system hinges on the integrity of its data and operational logic, yet this architecture faces persistent threats from malicious attacks. Data poisoning, where carefully crafted false information is introduced during the training phase, can subtly corrupt the system’s decision-making process, leading to unpredictable and potentially dangerous outcomes. Equally concerning are backdoor triggers – hidden functionalities intentionally inserted into the system that lie dormant until activated by a specific, attacker-defined input. These triggers allow adversaries to bypass normal security measures and manipulate the system’s behavior, compromising its safety and potentially causing significant harm. Recognizing and defending against both data poisoning and backdoor attacks is, therefore, paramount to ensuring the continued safe and dependable operation of these complex systems.
The system’s resilience against sophisticated attacks is significantly bolstered by the integrated TrustFED-LFD Module and Backdoor Attack Monitor Module. The TrustFED-LFD Module employs a federated learning defense, proactively identifying and neutralizing malicious data injections – known as data poisoning – that could compromise the model’s accuracy and safety. Simultaneously, the Backdoor Attack Monitor Module vigilantly scans for subtle, hidden triggers within the model – backdoors – that attackers could exploit to manipulate system behavior. These modules work in concert, providing a layered defense that not only detects anomalies but also actively mitigates threats, ensuring the continued reliability and safe operation of the entire system even under adversarial conditions. This dual-pronged approach is critical for maintaining trust and preventing unauthorized control or manipulation.
Maintaining the operational safety of complex systems demands a shift towards proactive security protocols, and machine unlearning emerges as a critical component of this defense. This technique doesn’t simply detect and react to malicious intrusions; it actively removes the influence of compromised data from the system’s learned models. By systematically ‘forgetting’ information potentially tainted by attacks – such as data poisoning attempts – machine unlearning prevents subtle, yet damaging, alterations to the system’s behavior. Unlike traditional methods that focus on patching vulnerabilities after an incident, this approach fortifies the system against future exploits by eliminating the lingering effects of past compromises, ensuring a more resilient and trustworthy operational framework.
Predictive Maintenance and Enduring System Resilience
The Equipment Health Monitor Module represents a significant advancement in operational intelligence, leveraging the power of IoT-driven equipment health monitoring to deliver crucial insights into the status of critical machinery and infrastructure. This module doesn’t simply report on current conditions; it establishes a baseline of normal operation and then continuously analyzes incoming data from a network of sensors. These sensors capture a wide range of parameters – vibration, temperature, pressure, and electrical current, among others – providing a holistic view of equipment performance. Through sophisticated algorithms and machine learning, the module identifies subtle anomalies that might indicate developing issues, enabling operators to move beyond reactive repairs and towards a predictive maintenance strategy. This granular level of monitoring extends the lifespan of valuable assets, optimizes performance, and minimizes costly disruptions caused by unexpected failures.
The Equipment Health Monitor Module significantly minimizes operational disruptions by shifting maintenance strategies from reactive repairs to preventative interventions. Through continuous data analysis, the module identifies subtle anomalies – deviations from expected performance – that often precede critical failures. This predictive capability allows maintenance teams to address issues before they escalate, scheduling repairs or replacements during planned downtime instead of responding to unexpected emergencies. Consequently, organizations experience a marked reduction in downtime, increased equipment lifespan, and optimized resource allocation, ultimately contributing to greater operational efficiency and cost savings.
The integration of the Equipment Health Monitor Module into a facility’s comprehensive safety architecture fundamentally shifts maintenance strategies from reactive responses to preventative action, bolstering overall system resilience. By seamlessly connecting real-time equipment condition data with existing safety protocols – such as automated shutdown procedures or controlled operational adjustments – the module allows for the anticipation and mitigation of potential failures before they escalate into critical incidents. This proactive approach not only minimizes costly downtime and repair expenses, but also significantly enhances operational efficiency by optimizing equipment performance and extending asset lifecycles. The result is a more robust and dependable infrastructure, capable of withstanding unforeseen challenges and maintaining consistent, safe operation.
The pursuit of robust autonomous systems, as detailed in this research concerning future mining, demands a foundation built upon provable correctness. The architecture proposed, integrating multimodal perception and delay-tolerant networking, strives for resilience not merely through empirical testing, but through inherent design principles. As Robert Tarjan once stated, “Data structures and algorithms are fundamental; they are the building blocks of all software.” This sentiment directly reflects the approach taken in this paper, where a unified system is constructed from rigorously defined components addressing connectivity limitations and adversarial threats. The emphasis on sensor fusion and predictive maintenance isn’t simply about achieving functionality, but establishing a system that can be demonstrably reliable even within unpredictable and challenging environments.
Beyond the Ore: Future Directions
The architecture presented here, while a pragmatic synthesis of existing techniques, merely scratches the surface of a fundamentally unsolved problem: reliable automation in truly unpredictable environments. The integration of Delay-Tolerant Networking, Federated Learning, and multimodal perception does not, in itself, create robustness; it simply offers a framework within which to approximate it. The critical limitation remains the inherent imperfection of all models, particularly when confronted with adversarial threats or unforeseen geological events. A predictive maintenance algorithm, however elegantly coded, is still a prediction – a statement of probability, not a guarantee.
Future work must therefore move beyond empirical validation and embrace formal verification. The field requires mathematically rigorous proofs of system safety and security, rather than simply demonstrating performance on curated datasets. Exploration of alternative learning paradigms – those less reliant on vast quantities of labeled data and more focused on symbolic reasoning – appears particularly promising. The pursuit of ‘generalizable’ intelligence within mining operations demands a shift in focus: from pattern recognition to the construction of verifiable, logically consistent models of the physical world.
Ultimately, the true test of this architecture – and indeed, of the entire field of autonomous mining – will not be its ability to extract resources efficiently, but its capacity to operate correctly – predictably and safely – even in the face of the inevitable imperfections of reality. The elegance of a system lies not in its complexity, but in the consistency of its boundaries and predictability.
Original article: https://arxiv.org/pdf/2602.11472.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- My Favorite Coen Brothers Movie Is Probably Their Most Overlooked, And It’s The Only One That Has Won The Palme d’Or!
- The Batman 2 Villain Update Backs Up DC Movie Rumor
- Adolescence’s Co-Creator Is Making A Lord Of The Flies Show. Everything We Know About The Book-To-Screen Adaptation
- Thieves steal $100,000 worth of Pokemon & sports cards from California store
- ‘Veronica’: The True Story, Explained
- Decoding Cause and Effect: AI Predicts Traffic with Human-Like Reasoning
- Future Assassin’s Creed Games Could Have Multiple Protagonists, Says AC Shadows Dev
- Moonpay’s New York Trust Charter: The Digital Gold Rush Gets Regulated! 🚀
- First Glance: “Wake Up Dead Man: A Knives Out Mystery”
- Exclusive: First Look At PAW Patrol: The Dino Movie Toys
2026-02-13 22:35