Author: Denis Avetisyan
A new review maps the complex web of technologies enabling the creation and dissemination of AI-generated sexual abuse material, revealing how efforts to combat it often feel like a futile game of whack-a-mole.
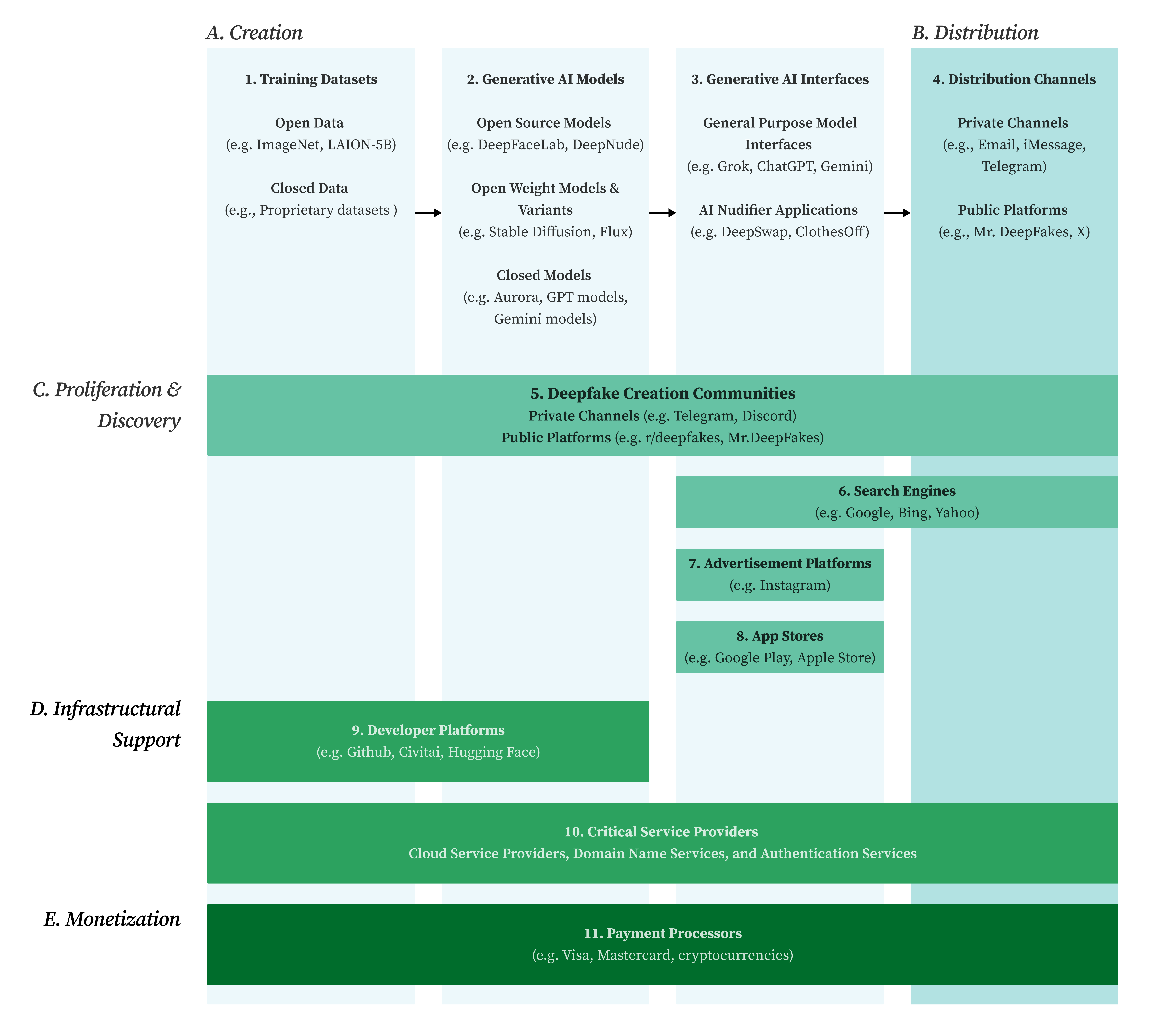
This paper presents a comprehensive ecosystem map of technologies facilitating AI-generated non-consensual intimate images and outlines potential interventions to disrupt their creation and spread.
Despite growing awareness of AI-generated non-consensual intimate images (AIG-NCII) as a form of image-based sexual abuse, interventions remain fragmented and reactive. This paper, ‘How to Stop Playing Whack-a-Mole: Mapping the Ecosystem of Technologies Facilitating AI-Generated Non-Consensual Intimate Images’, addresses this challenge by presenting the first comprehensive map of the 11 interconnected technology categories that enable the creation, dissemination, and monetization of AIG-NCII. Through a synthesis of over 100 primary sources, we demonstrate how this ecosystem map can be used to both understand emerging harms-as illustrated by a case study of Grok-and evaluate the efficacy of existing interventions. Can a shared understanding of this technological landscape finally move efforts beyond a perpetual cycle of response and toward proactive prevention?
Decoding the Digital Assault: The Rise of AI-Generated Harm
The advent of generative artificial intelligence has unlocked a disturbing new capacity: the creation of increasingly realistic and harmful non-consensual intimate imagery, often referred to as AIG-NCII. These models, trained on vast datasets, can fabricate highly convincing depictions of individuals in sexually explicit scenarios, even without their knowledge or consent. The resulting images are not simply crude forgeries; they exhibit a level of detail and plausibility that makes them profoundly damaging to the depicted individual’s reputation, emotional well-being, and potentially, their safety. This technology lowers the barrier to creating such content dramatically, moving beyond the need for photographic skill or direct manipulation of images, and instead relying on algorithmic generation, which poses significant risks to personal autonomy and dignity.
The rapid advancement and broad accessibility of generative artificial intelligence models have fostered an environment where the creation and dissemination of non-consensual intimate imagery (AIG-NCII) occurs at an alarming rate. Current estimates suggest that models like Grok AI are capable of generating thousands of such images every hour, highlighting the sheer scale of this emerging threat. This proliferation isn’t limited by technical expertise; user-friendly interfaces and readily available online access mean virtually anyone can generate highly realistic, fabricated intimate content. The combination of sophisticated AI and ease of use has created a landscape where the potential for harm is exponentially increased, far outpacing the ability of current preventative measures or legal frameworks to effectively respond.
Current legal structures, designed for traditional forms of image-based sexual abuse, are proving inadequate to address the unique challenges posed by AI-generated non-consensual intimate imagery. The sheer velocity at which these images can be created and disseminated-estimates suggest thousands are produced hourly-overwhelms existing reporting mechanisms and investigative capacities. Furthermore, establishing legal liability remains complex; attributing responsibility to the model’s developers, the user prompting the generation, or the platforms hosting the content presents novel legal questions. This jurisdictional ambiguity, coupled with the difficulty of proving intent and harm in the context of AI-generated content, often leaves victims with limited legal recourse and exacerbates the trauma associated with this rapidly evolving form of abuse. The lack of clear legal definitions and consistent enforcement across jurisdictions further compounds the problem, creating a landscape where perpetrators can operate with relative impunity and victims remain vulnerable.
Dissecting the Machine: The Architecture of Abuse
Generative artificial intelligence (AI) models require extensive training datasets to function; however, these datasets often contain harmful or non-consensual imagery and data sourced without explicit consent. This content is not necessarily limited to explicit material, but can include personally identifiable information, depictions of sensitive events, or biased representations. The inclusion of such data, whether accidental or deliberate, directly contributes to the creation of Abusive Image Generation – Non-Consensual Intimate Imagery (AIG-NCII) by providing the foundational material for the AI to learn and replicate. The scale of these datasets – often comprising billions of images and text pairings – makes manual vetting for problematic content impractical, increasing the risk of perpetuating harm through AI-generated outputs.
Generative AI interfaces, such as chat applications, image generation websites, and API access points, function as the primary means by which users interact with and create AI-Generated Non-Consensual Intimate Imagery (AIG-NCII). These interfaces abstract the complexities of underlying AI models, enabling individuals with limited technical expertise to easily generate content through text prompts or image uploads. This lowered barrier to entry significantly expands the potential pool of actors capable of creating AIG-NCII, as specialized knowledge of machine learning or programming is no longer a prerequisite. The ease of use, coupled with the increasing accessibility of these interfaces, directly contributes to the proliferation and scalability of malicious AIG-NCII creation and distribution.
This research identifies eleven technologies central to the AIG-NCII ecosystem, categorized as user interfaces, developer platforms, and essential service providers. User interfaces include platforms like Stable Diffusion’s web UI and image generation Discord bots, enabling prompt-based content creation. Developer platforms consist of model hosting services such as Hugging Face, and cloud computing providers like Amazon Web Services and Google Cloud Platform, which offer the infrastructure for model training and deployment. Critical service providers encompass data storage solutions, content delivery networks, and payment processors that collectively support the operation and scalability of AIG-NCII generation and distribution.
Breaking the Chain: Targeted Interventions and Early Victories
Payment processors are implementing enhanced due diligence procedures to identify and flag transactions associated with the creation and dissemination of Abusive Image Generation – Non-Consensual Intimate Imagery (AIG-NCII). This scrutiny extends to identifying merchants and accounts facilitating the purchase of computational resources, software licenses, and data sets used in AIG-NCII production. Consequently, malicious actors are experiencing increased difficulty accessing financial services necessary to sustain AIG-NCII operations, including challenges with processing subscription fees for relevant platforms and purchasing cloud computing time. These financial disruptions aim to reduce the economic viability of AIG-NCII creation and distribution by increasing operational costs and limiting access to essential resources.
The City of San Francisco’s lawsuit against developers of AI “nudifier” applications establishes a precedent for legal action regarding the enabling of harmful content creation. The suit alleges violations of California law concerning the unauthorized depiction of individuals in sexually explicit material, specifically targeting the developers for providing the technology that facilitates the creation of non-consensual intimate images. This legal challenge moves beyond simply addressing the distribution of AIG-NCII and instead focuses on the liability of those who create and provide the tools used in its production, signaling a shift towards holding technology developers accountable for foreseeable misuse and potentially establishing a legal framework for regulating the development of generative AI technologies with harmful applications.
The shutdown of MrDeepFakes in November 2023 demonstrated the effectiveness of targeting Critical Service Providers to disrupt the AIG-NCII ecosystem. MrDeepFakes, a prominent platform within Deepfake Creation Communities, relied on services like Cloudflare for content delivery and DDoS protection. Coordinated pressure, including legal notices and public appeals, led Cloudflare to terminate its services to the platform, effectively removing it from the internet. This action, impacting one of the 11 technologies identified as key to AIG-NCII proliferation, illustrates how disrupting infrastructural dependencies – beyond directly addressing content – can dismantle platforms facilitating the creation and distribution of harmful deepfakes. The incident highlights the vulnerability of these communities to disruptions targeting essential service providers and the potential for cascading effects within the broader ecosystem.
Rewriting the Rules: Legal Frameworks and the Ethics of Creation
The TAKE IT DOWN Act establishes a vital mechanism for individuals subjected to the deeply harmful practice of non-consensual intimate image sharing. This legislation empowers victims to directly petition Distribution Channels – encompassing websites, social media platforms, and messaging services – to swiftly remove illegally posted images or videos. Prior to the Act, victims often faced significant hurdles, navigating complex legal processes or relying on unresponsive platforms. The law creates a clear legal pathway, demanding a prompt response from these channels and, if unsuccessful, opening them up to potential legal repercussions. This shift not only provides recourse for those affected but also incentivizes platforms to proactively address the issue and implement preventative measures, fostering a safer online environment and recognizing the severe emotional and psychological distress caused by this form of digital abuse.
Digital distribution channels, particularly those accessed through app stores, have become central battlegrounds in addressing the proliferation of illegally shared intimate images. While major app stores now possess policies prohibiting such content and mechanisms for reporting and removal, the efficacy of these systems varies considerably. Research indicates a growing trend of app stores assuming a more proactive role in content moderation, utilizing both automated detection tools and human review processes. However, inconsistencies in enforcement – stemming from differing interpretations of policies, resource limitations, and varying responsiveness to reports – remain a significant challenge. This uneven application of rules creates a fragmented landscape where victims often face substantial hurdles in securing the removal of harmful content, underscoring the need for greater standardization and transparency in app store policies and practices.
A comprehensive synthesis of over 100 sources reveals the complex and rapidly evolving landscape of Abusive Image-based Sexual Abuse (AIG-NCII). This research delves into the legal challenges, technological advancements, and societal impacts surrounding the non-consensual sharing of intimate images, establishing a detailed understanding of the problem’s scope and its harms. The findings directly inform the development of effective legal frameworks designed to protect victims and hold perpetrators accountable. Furthermore, the study offers actionable insights for Distribution Channels and tech companies, guiding them toward responsible content moderation policies and proactive measures to prevent the spread of abusive imagery, ultimately fostering a safer digital environment.
The analysis detailed within the ecosystem map resembles a complex system begging for deconstruction. It isn’t enough to simply identify the tools facilitating AI-generated Non-Consensual Intimate Images (AIG-NCII); one must understand how they interconnect, and more crucially, where the vulnerabilities lie. As Claude Shannon observed, “The most important thing in communication is to get the message across, not necessarily to understand it.” This rings true here – the ‘message’ of AIG-NCII is being ‘communicated’ with devastating effectiveness, yet understanding the underlying technological infrastructure – the generative AI ecosystem – remains a critical, often overlooked, challenge. Breaking down this system, mapping its flows, and identifying the weak points allows for targeted interventions, turning passive observation into active disruption.
Beyond Whack-a-Mole
The presented ecosystem map isn’t an endpoint, but rather a detailed schematic for future disassembly. It reveals the predictable architecture of abuse – the modularity of generative AI, the vulnerabilities of content hosting platforms, the inherent lag in detection methodologies. The exercise isn’t about eliminating these components-that’s a futile game of suppression. It’s about understanding how they connect, the points of leverage where intervention isn’t simply reactive patching, but proactive redirection.
Current efforts largely treat AIG-NCII as a content problem. The map suggests this is a misdiagnosis. The problem resides in the flow-the frictionless transfer of capability from research to application, the algorithmic amplification of harmful content, the economic incentives that reward virality over consent. Future research should focus less on perfecting deepfake detection – an escalating arms race – and more on disrupting this flow, on introducing friction at systemic levels.
Ultimately, the true test of this work lies not in its descriptive accuracy, but in its capacity to be rendered obsolete. If the map accurately charts the landscape of abuse, successful countermeasures will fundamentally alter that landscape, demanding a new cartography. This isn’t about winning a war; it’s about understanding the rules of the game well enough to rewrite them.
Original article: https://arxiv.org/pdf/2602.04759.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- All Golden Ball Locations in Yakuza Kiwami 3 & Dark Ties
- Hollywood is using “bounty hunters” to track AI companies misusing IP
- Gold Rate Forecast
- What time is the Single’s Inferno Season 5 reunion on Netflix?
- NBA 2K26 Season 5 Adds College Themed Content
- A Knight Of The Seven Kingdoms Season 1 Finale Song: ‘Sixteen Tons’ Explained
- Mario Tennis Fever Review: Game, Set, Match
- 4. The Gamer’s Guide to AI Summarizer Tools
- A free trip to the Moon will soon be possible. This upcoming exploration simulator is all about scientific realism
- This free dating sim lets you romance your cleaning products
2026-02-06 06:53