Author: Denis Avetisyan
A new Edge-Local-Cloud architecture, DMind-3, promises safer, faster, and more private transaction execution by prioritizing user control and robust verification.
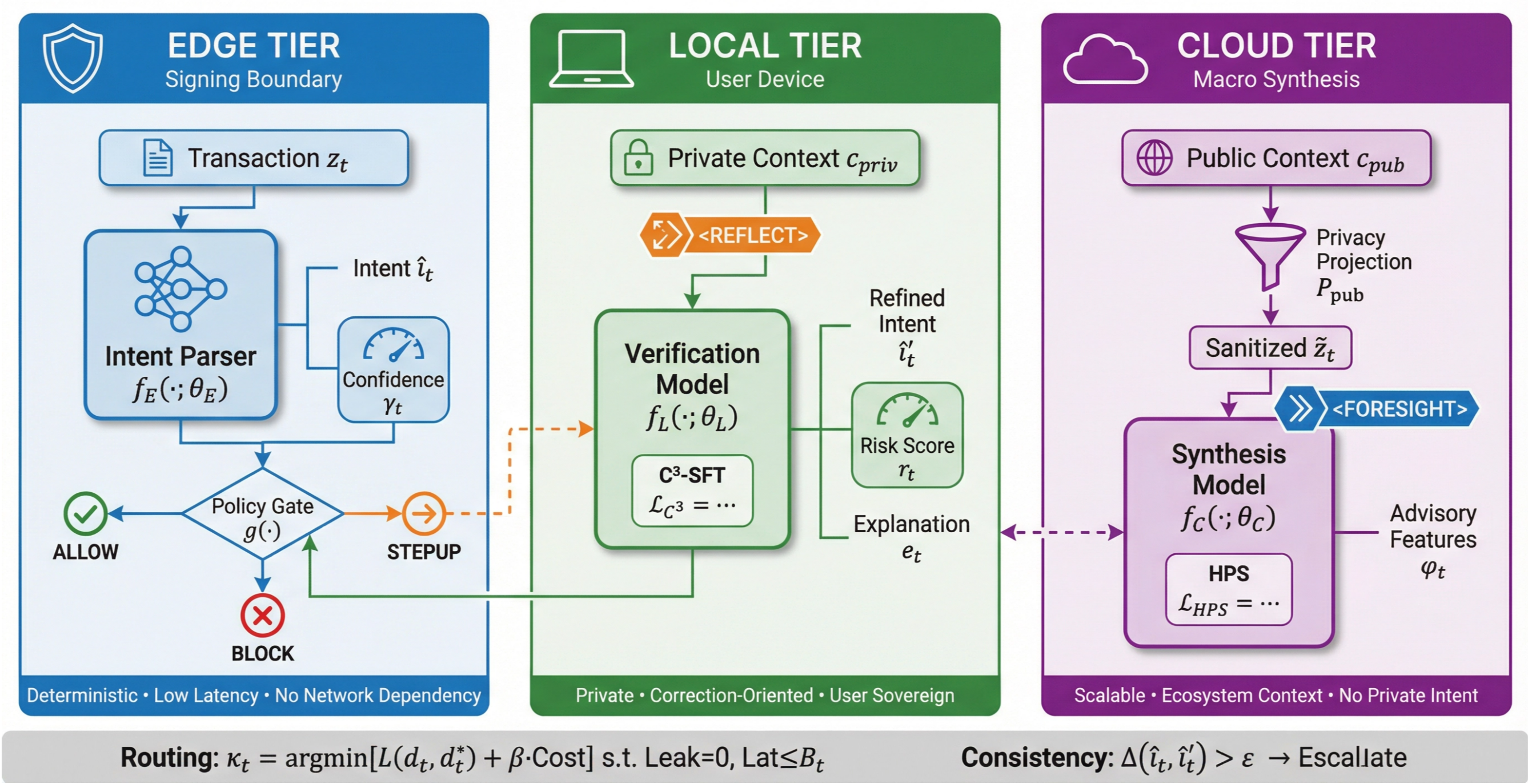
DMind-3 employs controlled deliberation and correction-based tuning to build sovereign AI agents for enhanced Web3 security and low-latency performance.
Existing AI assistants for Web3 environments often struggle to balance privacy, reliability, and latency under adversarial conditions. This paper introduces ‘DMind-3: A Sovereign Edge–Local–Cloud AI System with Controlled Deliberation and Correction-Based Tuning for Safe, Low-Latency Transaction Execution’, a novel architecture that decomposes intelligence across edge, local, and cloud layers to secure irreversible financial transactions. DMind-3 achieves a 93.7% success rate in constrained tasks by prioritizing safety at the signing boundary and employing techniques like Hierarchical Predictive Synthesis and Contrastive Chain-of-Correction Supervised Fine-Tuning to enhance local verification. Can this approach establish a new paradigm for building sovereign AI agents capable of navigating the complexities of decentralized finance with enhanced security and user control?
The Inevitable Erosion of Trustless Systems
The ambition of Web3 finance centers on constructing a financial ecosystem liberated from traditional intermediaries, relying instead on self-executing smart contracts and decentralized exchanges (DEXs). However, this emergent landscape isn’t without significant vulnerabilities, as demonstrated by analyses termed ‘Flash Boys 2.0’. These investigations reveal that the very openness and transparency of blockchain systems can be exploited by sophisticated actors who leverage their speed and access to information to front-run transactions – essentially, inserting their own trades ahead of others to profit from predictable price movements. This manipulation isn’t necessarily illegal, but it erodes trust and raises concerns about fair access within the decentralized financial space, prompting a search for mechanisms to ensure equitable execution and mitigate these adversarial dynamics.
The bedrock of many Web3 financial systems, the Nakamoto Consensus – responsible for confirming transactions on blockchains like Bitcoin – prioritizes preventing double-spending and ensuring data integrity, but doesn’t automatically safeguard against more subtle forms of manipulation. While effectively establishing a shared, immutable ledger, this consensus mechanism doesn’t inherently address predatory practices like frontrunning or ‘sandwich attacks’ where malicious actors exploit knowledge of pending transactions. These adversarial dynamics arise because the consensus process itself doesn’t guarantee fair execution, only valid execution; a transaction can be valid according to the rules of the blockchain yet still disadvantage others. Consequently, developers are actively exploring supplementary mechanisms – layered on top of the Nakamoto Consensus – to provide additional safeguards and ensure a more equitable environment for decentralized finance.
Traditional security architectures in finance rely on centralized intermediaries to guarantee transaction order and prevent manipulation, but these models are fundamentally at odds with the core tenets of Web3. Decentralized systems, by design, distribute trust across a network, making it exceedingly difficult to establish a single, authoritative source for execution guarantees. This creates a tension: while decentralization enhances resilience against censorship and single points of failure, it simultaneously introduces new vulnerabilities related to transaction ordering – such as frontrunning – and the potential for malicious actors to exploit latency or network congestion. Current cryptographic techniques and consensus mechanisms, while addressing data integrity, often fall short in providing the precise, deterministic execution required for complex financial instruments, leaving decentralized finance susceptible to subtle but significant forms of market manipulation and requiring innovative approaches to reconcile security with the promise of a trustless ecosystem.
DMind-3: Architecting Sovereignty in a Volatile Landscape
DMind-3 is a novel intelligence stack architected for financial applications within Web3 environments, distinguished by its sovereign design and tiered Edge-Local-Cloud structure. This stack prioritizes autonomous operation and data control, enabling execution of financial strategies without reliance on external, centralized services. The architecture distributes computational tasks across three layers: Edge devices for immediate data processing and pre-filtering; Local servers for secure, low-latency analysis and decision-making; and Cloud infrastructure for model training, data storage, and complex computations. This distribution is specifically intended to facilitate adversarial financial execution, implying an ability to react to and potentially exploit market inefficiencies or vulnerabilities, all while maintaining data sovereignty and minimizing external dependencies.
DMind-3’s tiered architecture distributes computational tasks across Edge, Local, and Cloud environments to enhance both security and privacy. Edge processing handles initial data acquisition and pre-processing, minimizing data transmission. Sensitive computations and private key management are confined to the Local tier, operating on user-controlled hardware and isolated networks. The Cloud tier facilitates computationally intensive tasks and model updates, benefiting from scalability and access to broader datasets, but only receives anonymized or aggregated data. This distribution minimizes the attack surface by reducing centralized data storage and limiting exposure of sensitive information, while also optimizing for latency and bandwidth constraints inherent in Web3 applications.
DMind-3 employs Policy-Driven Selective Offloading to dynamically allocate computational tasks across Edge, Local, and Cloud resources. This optimization is based on three key factors: data sensitivity, required latency, and computational uncertainty. Sensitive data remains on-device or within a secure Local environment, while latency-critical operations are prioritized for Edge execution. Tasks with high uncertainty or requiring significant resources are offloaded to the Cloud. This tiered approach enables a functional architecture achieving a 99th percentile (p99) latency of under 50 milliseconds, balancing security, privacy, and performance for Web3 financial applications.
Firewalling the Periphery: A Multi-Layered Defense
The Edge Tier functions as the initial point of defense by employing an Intent Firewall to analyze incoming transactions. This firewall operates by parsing transaction requests and comparing them against a pre-defined set of deterministic safety rules. These rules are designed to identify and block potentially harmful or invalid operations before they can propagate further into the system. The deterministic nature of these rules ensures predictable and consistent enforcement, eliminating ambiguity in security decisions. This approach focuses on preventing violations by explicitly defining acceptable behavior, rather than relying on reactive detection mechanisms.
Data sanitization within the system is implemented across all layers of the processing stack to mitigate risks to user privacy and prevent data leakage. These techniques encompass a range of methods, including data masking, redaction, and encryption, applied both in transit and at rest. Performance evaluations demonstrate that, under standard operating policies, data violation rates are rare. Furthermore, the implementation of stricter data handling policies results in effectively eliminating detectable data violations, as verified through internal auditing and security testing. This multi-layered approach ensures continuous protection of sensitive information throughout its lifecycle within the system.
The Risk-Aware Orchestration Plane maintains a complete audit trail of all transactions, recording data origin and modification history to establish comprehensive provenance. This plane performs consistency checks at multiple stages, verifying data integrity and adherence to defined policies. When the system encounters anomalous data or inconsistencies, or when confidence in data validity falls below a configured threshold, the Orchestration Plane automatically escalates verification requirements. This escalation can involve more rigorous data validation, increased sampling rates, or the invocation of additional security protocols, ensuring a dynamic and adaptive security posture.
Controlled Deliberation within the system enables dynamic adjustment of verification intensity, prioritizing speed or security as required. This is achieved through a switching mechanism between fast and thorough verification modes, allowing for efficient processing of routine transactions while reserving more comprehensive analysis for potentially risky operations. Benchmarking with DMind-3 demonstrates a 93.7% success rate in multi-turn structured interactions, indicating reliable performance in complex, iterative verification scenarios. This adaptive approach balances operational efficiency with a robust security posture by allocating resources proportionally to the assessed risk level.
The Dawn of Decentralized Intelligence: Federated Learning and Beyond
DMind-3 distinguishes itself through an architecture specifically designed to support Federated Learning, a paradigm shift in how machine learning models are trained. Instead of centralizing sensitive data, this approach allows model training to occur directly on decentralized datasets – such as those held by individual financial institutions or users – without ever requiring the data to leave its source. This is achieved through a sophisticated system of local model training and aggregation of model updates, ensuring that raw data remains private and secure. The resulting globally-informed model benefits from a broader, more diverse dataset, while simultaneously upholding stringent privacy standards – a critical advancement for industries handling confidential financial information and increasingly important in a landscape prioritizing data sovereignty.
The integration of machine learning within the Web3 ecosystem is significantly advanced through DMind-3, creating pathways for novel financial applications and decentralized intelligence. This system doesn’t merely apply existing models; it demonstrably surpasses current state-of-the-art language models like GPT-5.1, achieving a +2.2 improvement on the DMind Benchmark – a metric assessing comprehensive AI capabilities – and a +1.9 increase on the FinanceQA benchmark, specifically evaluating financial reasoning. These performance gains aren’t incremental; they suggest a fundamental leap in the ability to process and understand complex financial data, potentially enabling automated trading strategies, enhanced risk assessment, and personalized financial services – all within a secure, decentralized framework.
DMind-3 establishes a pathway towards a more secure and dependable financial ecosystem by integrating decentralized intelligence with advanced security protocols. This system doesn’t rely on centralized data repositories, mitigating risks associated with single points of failure and enhancing data privacy. Notably, the DMind-3-mini variant demonstrates that robust performance isn’t sacrificed for efficiency; it maintains 94.9% of the DMind Benchmark score and 92.7% of the FinanceQA score while operating with a significantly reduced computational footprint. This scalability is crucial for wider adoption, allowing for deployment across a diverse range of devices and infrastructures, and ultimately fostering a financial future built on trust and resilience.
The development of DMind-3, with its emphasis on controlled deliberation and correction-based tuning, mirrors a fundamental tenet of resilient system design. Grace Hopper observed, “It’s easier to ask forgiveness than it is to get permission.” This sentiment resonates deeply with DMind-3’s architecture, which prioritizes proactive safety at the signing boundary while allowing for localized correction of potential errors. The system doesn’t seek to prevent all issues, but rather to contain them swiftly and efficiently within the Edge-Local-Cloud framework. This approach acknowledges that incidents are inevitable steps towards maturity, aligning with the philosophy that systems are not static entities but continuously evolving processes adapting within the medium of time.
What Lies Ahead?
DMind-3 addresses a critical juncture: the need for robust, localized agency within increasingly complex Web3 systems. However, the pursuit of ‘sovereignty’ itself introduces a new class of decay. Any system claiming absolute control inevitably encounters the limits of its own predictive capacity, becoming brittle in the face of unforeseen interactions. The architecture, while prioritizing safety at the signing boundary, merely pushes the point of failure further downstream – a temporary reprieve, not a permanent solution. Technical debt, in this context, is not a bug to be fixed, but erosion – an inevitable consequence of operating within a dynamic, adversarial environment.
Future work must acknowledge that ‘correction-based tuning’ is not a destination, but a continuous process of adaptation. The real challenge lies in designing systems that gracefully degrade, minimizing harm as their internal models drift from reality. Investigating the interplay between localized edge processing and the broader cloud infrastructure will be crucial, particularly concerning the emergence of unpredictable latency. Uptime, after all, is a rare phase of temporal harmony, not a sustainable state.
Ultimately, the success of systems like DMind-3 will not be measured by their ability to prevent failure, but by their capacity to contain it. The focus should shift from building impenetrable fortresses to cultivating resilient ecosystems-systems that learn from disruption and evolve alongside the inevitable currents of change.
Original article: https://arxiv.org/pdf/2602.11651.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Movie Games responds to DDS creator’s claims with $1.2M fine, saying they aren’t valid
- SHIB PREDICTION. SHIB cryptocurrency
- Scream 7 Will Officially Bring Back 5 Major Actors from the First Movie
- United Airlines can now kick passengers off flights and ban them for not using headphones
- The MCU’s Mandarin Twist, Explained
- These are the 25 best PlayStation 5 games
- Rob Reiner’s Son Officially Charged With First Degree Murder
- Server and login issues in Escape from Tarkov (EfT). Error 213, 418 or “there is no game with name eft” are common. Developers are working on the fix
- MNT PREDICTION. MNT cryptocurrency
- Gold Rate Forecast
2026-02-14 16:57