Author: Denis Avetisyan
A new approach harnesses the power of language models and Siamese networks to identify previously unseen attacks targeting vulnerable IoT devices.
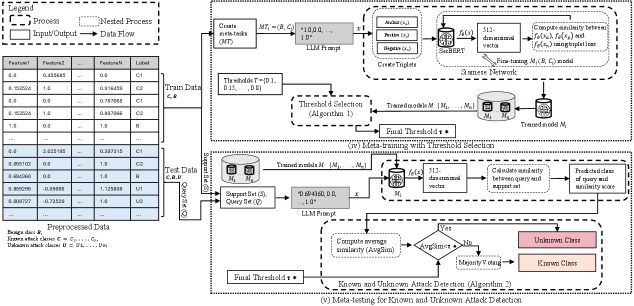
This review details SiamXBERT, a data-efficient method for unknown attack detection in IoT networks leveraging SecBERT and cross-dataset generalization.
Detecting novel cyberattacks remains a critical challenge in the rapidly expanding landscape of Internet of Things (IoT) networks, often hampered by data scarcity and the increasing use of encrypted traffic. This paper, ‘Unknown Attack Detection in IoT Networks using Large Language Models: A Robust, Data-efficient Approach’, introduces SiamXBERT, a Siamese meta-learning framework leveraging transformer-based language models to effectively identify previously unseen attacks. By integrating flow- and packet-level information, SiamXBERT achieves superior performance and generalization capabilities-demonstrating up to a 78.8\%\ improvement in unknown attack F1-score-while requiring significantly less training data than existing methods. Could this data-efficient approach pave the way for more resilient and adaptable IoT security solutions in real-world deployments?
The Expanding Horizon of Vulnerability
The exponential growth of Internet of Things (IoT) devices presents an increasingly complex challenge to cybersecurity. As interconnected systems permeate critical infrastructure – from patient monitoring in healthcare and autonomous functions in transportation to the convenience of smart homes – the potential avenues for malicious actors to exploit vulnerabilities multiply. Each newly deployed device represents a potential entry point, effectively expanding the “attack surface” and creating a broader range of targets for compromise. This proliferation isn’t simply a matter of increased numbers; the sheer diversity of these devices, often manufactured with limited security considerations and varying lifecycles, introduces a fragmented and heterogeneous landscape that is difficult to comprehensively protect. Consequently, a single compromised device can potentially serve as a pivot point, granting unauthorized access to entire networks and systems, with potentially devastating consequences.
Conventional cybersecurity approaches, designed to detect and block threats based on pre-defined attack signatures, are increasingly ineffective against the rapidly expanding landscape of interconnected devices. These systems often struggle to identify zero-day exploits and polymorphic malware – threats that constantly evolve to evade detection – due to their reliance on recognizing known malicious patterns. The sheer diversity of IoT devices, each with unique vulnerabilities and software configurations, further exacerbates this problem, creating a fragmented security posture where novel attacks can easily bypass traditional defenses. Consequently, security solutions must shift towards behavioral analysis and anomaly detection, focusing on identifying malicious activity rather than simply recognizing known threats, to adequately protect these vulnerable systems.
The increasing reliance on encryption to protect data traversing the Internet of Things presents a significant challenge for network security. While crucial for confidentiality, this widespread adoption effectively creates a ‘blind spot’ for traditional intrusion detection systems. These systems typically operate by inspecting the contents – the payload – of network packets for known malicious patterns; however, encrypted traffic renders this process impossible without first decrypting the data. This decryption process is often impractical due to computational overhead and privacy concerns, and even when feasible, requires careful key management. Consequently, sophisticated attacks can now be concealed within seemingly legitimate, encrypted communications, bypassing conventional security measures and making the identification of malicious activity substantially more difficult. This necessitates the development of new security approaches, such as encrypted traffic analysis and machine learning-based anomaly detection, to effectively address the evolving threat landscape.
The Limits of Pattern Recognition
Machine learning (ML) and deep learning (DL) models for intrusion detection are primarily pattern-recognition systems trained on datasets of previously identified malicious activity. Consequently, their efficacy is maximized when encountering attacks that closely resemble those present in the training data. However, these models struggle with zero-day exploits and polymorphic threats, which by design deviate from established signatures. This limitation arises because ML/DL algorithms extrapolate from existing examples; they are not inherently capable of identifying behaviors that fall outside the scope of their training. Furthermore, adversarial attacks – specifically crafted inputs designed to evade detection – can exploit vulnerabilities in the learned patterns, rendering these models ineffective against novel, albeit subtly modified, threats.
Traditional machine learning models for IoT security require substantial volumes of accurately labeled data for training, a process that presents significant logistical and financial challenges. Data labeling is labor-intensive, demanding skilled analysts to identify and categorize network traffic or system behavior as either benign or malicious. Furthermore, the rapidly evolving threat landscape necessitates continuous data collection and re-labeling; as attackers develop new techniques and exploit previously unknown vulnerabilities, existing labeled datasets become quickly outdated and ineffective at detecting novel attacks. This constant need for updated, labeled data creates a continuous operational expense and represents a key limitation in maintaining effective security postures for IoT devices and networks.
The reliance of traditional machine learning models on pre-defined attack signatures and labeled datasets inherently limits their ability to detect novel threats. This creates a significant security gap for IoT systems because zero-day exploits, by definition, are attacks that have not been previously observed and therefore lack corresponding signatures in training data. Consequently, these systems are unable to generalize to previously unseen attack vectors, leaving devices and networks vulnerable to compromise until new signatures can be developed and models retrained – a process which introduces a critical delay in mitigation and allows for widespread exploitation during the interim period.
SiamXBERT: Recognizing the Unseen
SiamXBERT leverages the strengths of both Siamese Networks and the SecBERT transformer model for improved unknown IoT attack detection. The Siamese Network architecture learns a function to determine the similarity between two input network traffic samples, enabling anomaly detection by identifying deviations from established normal behavior without requiring prior knowledge of specific attack signatures. This is coupled with the SecBERT model, a transformer-based architecture pre-trained on network security data, to extract robust and contextualized features from network traffic. By combining these two approaches, SiamXBERT creates a system capable of generalizing to previously unseen attacks and effectively distinguishing malicious activity from benign network communication.
The SiamXBERT model leverages a Siamese Network to establish a baseline of normal network behavior by learning a similarity metric between network traffic samples. This network consists of two identical sub-networks that process input data and output an embedding vector representing the traffic’s characteristics. The distance between these embedding vectors is then calculated; smaller distances indicate high similarity to known normal traffic. Anomalous traffic, representing previously unseen attacks, will produce larger distances due to its deviation from the learned normal behavior, allowing for detection without requiring pre-defined attack signatures or prior knowledge of specific threat profiles. This approach focuses on identifying outliers based on inherent differences in traffic patterns rather than matching known malicious indicators.
Feature importance selection within the SiamXBERT model is achieved through permutation importance, evaluating each input feature’s contribution to the model’s overall performance by measuring the decrease in accuracy when the feature is randomly shuffled. This process identifies the most salient features for attack detection, allowing the model to focus on the most informative data points and discard irrelevant noise. Following feature selection, careful thresholding is applied to the similarity scores output by the Siamese Network. This involves establishing an optimal threshold value – determined through validation on a representative dataset – above which network traffic is flagged as anomalous. Rigorous threshold calibration is crucial; a higher threshold minimizes false positives but risks missing genuine attacks, while a lower threshold increases detection rates at the expense of generating more false alarms. The combined effect of feature importance selection and optimized thresholding significantly improves the model’s precision and recall, leading to more accurate and reliable unknown attack detection.
The SiamXBERT model leverages both flow-level and packet-level network features to improve attack detection accuracy. Flow-level features, such as duration, packet count, and byte counts, provide a broad overview of network communication patterns. Complementing this, packet-level features – including protocol types, flags, and payload characteristics – offer granular details about individual packets. Combining these feature sets allows the model to capture both macro-level traffic anomalies and subtle deviations within packet data, resulting in a more comprehensive understanding of network behavior and a strengthened ability to identify previously unknown attacks compared to systems utilizing only one type of feature.
Validation Across Shifting Sands
Cross-dataset evaluation of SiamXBERT, utilizing datasets CICIoT2023 and IoT-23, confirms its capacity to generalize to previously unseen data while maintaining high detection accuracy. In these evaluations, the model achieved an F1-score of 81.6% for detecting unknown attacks. This indicates a strong ability to identify malicious activity not present in the training data, suggesting robustness against zero-day exploits and evolving threat landscapes. The methodology employed prioritized assessing performance on independent datasets to provide a realistic measure of the model’s adaptability and overall effectiveness in practical deployment scenarios.
SiamXBERT’s performance benefits from the integration of Zeek and DPKT for network traffic analysis. Zeek, a powerful network security monitoring framework, facilitates deep packet inspection and the extraction of relevant features from network flows. DPKT, a Python-based packet parsing library, provides a fast and reliable method for dissecting packet data. These tools enable the extraction of a comprehensive set of features – including protocol information, flow statistics, and payload characteristics – which are then used as input to the SiamXBERT model. The accurate and detailed feature extraction facilitated by Zeek and DPKT directly contributes to the model’s ability to effectively distinguish between benign traffic and malicious attacks.
The implementation of complementary techniques alongside SiamXBERT strengthens its defensive capabilities against evolving threats. SAFE-NID provides a framework for network intrusion detection, while ACGAN (Adversarial Convolutional Generative Adversarial Network) enhances the model’s ability to detect novel attacks by generating synthetic adversarial examples for training. Integration with the existing IDS-Agent further refines detection accuracy and provides a layered security approach; these combined methodologies address limitations inherent in single-model deployments and improve overall robustness against previously unseen attack vectors.
Comparative analysis demonstrates SiamXBERT’s superior performance against the IDS-Agent baseline. On the CICIoT2023 dataset, SiamXBERT achieved an improvement of 78.8% in detection accuracy, while on the IoT-23 dataset, the improvement reached approximately 415.4%. Notably, this performance was attained using a significantly reduced training dataset; SiamXBERT was trained with only 100 labeled samples per attack class, indicating a high degree of data efficiency and potential for deployment in resource-constrained environments.
Validation of SiamXBERT across datasets CICIoT2023 and IoT-23 demonstrates its adaptability to unseen network traffic characteristics, indicating potential for real-world deployment in diverse IoT environments. The model achieved an 81.6% F1-score in cross-dataset unknown attack detection, and outperformed a baseline IDS-Agent by 78.8% on CICIoT2023 and 415.4% on IoT-23, despite being trained with only 100 labeled samples per class. This performance, coupled with efficient training requirements, suggests SiamXBERT offers a viable and dependable solution for securing a broad range of Internet of Things deployments.
Towards a Proactive Defense
Traditional IoT security often relies on signature-based detection, a reactive approach that identifies threats by matching known patterns. However, the rapidly evolving landscape of cyberattacks demands a shift towards more intelligent defenses. Recent advancements, such as the successful implementation of the SiamXBERT model, demonstrate the efficacy of adaptive and proactive security solutions. SiamXBERT’s ability to learn nuanced representations of network traffic allows it to identify anomalous behavior indicative of novel attacks, even without prior knowledge of specific signatures. This represents a significant leap forward, enabling security systems to anticipate and neutralize threats before they can compromise devices or networks. By focusing on behavioral analysis and machine learning, future IoT security will prioritize identifying malicious intent rather than simply recognizing pre-defined attack patterns, ultimately bolstering the resilience of interconnected systems.
The escalating diversity and volume of Internet of Things devices present a significant challenge for traditional machine learning security approaches, which often require extensive labeled datasets for effective threat detection. Consequently, future advancements hinge on the integration of meta-learning techniques, allowing models to learn how to learn from limited data. This “learning to learn” capability enables rapid adaptation to previously unseen attack patterns with minimal new training examples – a crucial advantage in the dynamic landscape of IoT threats. By effectively leveraging prior knowledge and quickly generalizing from scarce data, meta-learning promises to bolster the resilience of IoT ecosystems against novel and evolving cyberattacks, offering a proactive defense mechanism that surpasses the limitations of signature-based or conventionally trained models.
The development of truly resilient Internet of Things ecosystems hinges on the synergistic integration of advanced machine learning and rapidly updated threat intelligence. Current security measures often struggle against novel attacks, but combining predictive modeling with real-time data streams allows for a dynamic defense. Machine learning algorithms can analyze network traffic, device behavior, and vulnerability reports to identify anomalous patterns indicative of malicious activity. This analysis, when coupled with the latest threat intelligence – including known attack signatures, emerging vulnerabilities, and attacker tactics – enables proactive threat mitigation. The result is a system capable of not only detecting sophisticated attacks but also anticipating and preventing them, ultimately fostering a more secure and trustworthy interconnected world where devices can operate with greater reliability and user privacy is prioritized.
The proliferation of interconnected devices, while offering unprecedented convenience and efficiency, simultaneously expands the attack surface for malicious actors, making continued innovation in IoT security not merely beneficial, but essential. As billions more devices join the Internet of Things, the potential consequences of successful attacks – ranging from compromised personal data to disruptions of critical infrastructure – escalate dramatically. Addressing these challenges requires a sustained commitment to research and development, focused on proactive defense mechanisms and adaptive security protocols. This ongoing effort is vital to safeguard the privacy of individuals and maintain the stability of increasingly digitalized systems, ultimately ensuring trust and fostering continued growth within the interconnected world.
The pursuit of robust anomaly detection, as detailed in this work, acknowledges the inherent temporality of system security. While SiamXBERT strives for enhanced cross-dataset generalization, it operates within the inevitable decay of any protective measure. Grace Hopper famously stated, “It’s easier to ask forgiveness than it is to get permission.” This sentiment reflects the proactive, yet adaptive, nature of securing IoT networks. The model, much like a swift response to a security breach, prioritizes action even with incomplete information, understanding that absolute, preemptive stability is an illusion cached by time. The continuous evolution of attacks necessitates a similar agility in defense, embracing a philosophy of iterative improvement over static perfection.
What Lies Ahead?
The pursuit of anomaly detection in IoT networks, as exemplified by SiamXBERT, reveals a familiar pattern: each commit a record in the annals, and every version a chapter in a story perpetually rewritten. This work addresses the immediate challenge of unknown attacks, yet the inherent limitations of any signature-less system remain. The very act of defining ‘normal’ is a transient exercise; devices evolve, networks reconfigure, and the baseline shifts beneath one’s feet. Delaying fixes, in essence, is a tax on ambition-a deferral of the inevitable entropy.
Future iterations will inevitably focus on refining the meta-learning process. The question isn’t simply about achieving higher accuracy on benchmark datasets, but about building systems that gracefully degrade as the threat landscape mutates. Exploring the integration of unsupervised learning techniques – allowing the network to construct its own understanding of ‘normal’ without constant human intervention – presents a compelling, if arduous, path.
Ultimately, the true metric of success will not be the number of attacks detected, but the number of anticipated disruptions. The field must move beyond reactive measures and towards predictive models capable of adapting to the unseen, acknowledging that in the realm of security, time isn’t a measure of progress, but the medium in which all systems inevitably decay.
Original article: https://arxiv.org/pdf/2602.12183.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- United Airlines can now kick passengers off flights and ban them for not using headphones
- SHIB PREDICTION. SHIB cryptocurrency
- Movie Games responds to DDS creator’s claims with $1.2M fine, saying they aren’t valid
- Scream 7 Will Officially Bring Back 5 Major Actors from the First Movie
- The MCU’s Mandarin Twist, Explained
- These are the 25 best PlayStation 5 games
- Server and login issues in Escape from Tarkov (EfT). Error 213, 418 or “there is no game with name eft” are common. Developers are working on the fix
- Rob Reiner’s Son Officially Charged With First Degree Murder
- MNT PREDICTION. MNT cryptocurrency
- Gold Rate Forecast
2026-02-15 06:21