Author: Denis Avetisyan
A new framework leverages the power of artificial intelligence to predict and prevent disruptions in critical communication infrastructure.
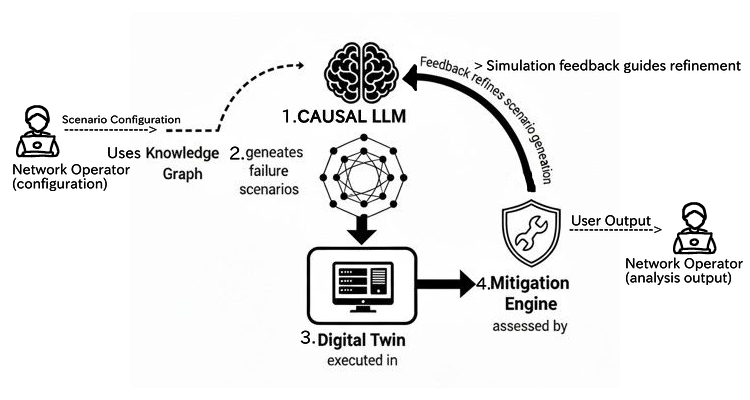
This review explores the use of causal language models and digital twins to generate adversarial scenarios and proactively mitigate potential failures in telecom networks.
Telecom networks face increasing complexity, yet current failure mitigation strategies remain largely reactive. This paper introduces ‘Adversarial Network Imagination: Causal LLMs and Digital Twins for Proactive Telecom Mitigation’, a novel framework designed to anticipate and address network vulnerabilities before service degradation occurs. By integrating a Causal Large Language Model, a Knowledge Graph, and a Digital Twin, the approach proactively generates and simulates realistic, adversarial failure scenarios to evaluate mitigation strategies. Could this shift from reactive troubleshooting to anticipatory resilience analysis fundamentally reshape network operations and improve service reliability?
The Inevitable Cascade: Understanding Network Fragility
The escalating complexity of modern networks-driven by virtualization, cloud computing, and the proliferation of interconnected devices-introduces vulnerabilities to cascading failures. These systems, while offering unprecedented scalability and flexibility, often lack the inherent robustness of their predecessors; a single compromised node or overloaded link can initiate a chain reaction, propagating disruptions across the entire infrastructure. This susceptibility isn’t simply a matter of increased scale, but arises from the intricate interdependencies within these networks, where the failure of one component can unexpectedly trigger a series of subsequent failures. Consequently, identifying and mitigating these single points of weakness becomes paramount, requiring a departure from traditional, localized troubleshooting methods toward holistic risk assessment and proactive resilience strategies.
Historically, assessing network vulnerability has depended on painstakingly constructed failure scenarios – imagined disruptions designed by human engineers. This approach, while valuable, inherently suffers from a critical limitation: it can only test for what is anticipated. The sheer complexity of modern networks, with countless interconnected components and dynamic traffic patterns, means that a vast number of potential failure modes remain unexplored. These manually crafted tests often fail to account for the subtle interactions between systems, the unpredictable nature of user behavior, or the emergence of unforeseen vulnerabilities. Consequently, networks remain susceptible to cascading failures triggered by events that were never considered during the initial risk assessment, highlighting the need for more comprehensive and automated testing methodologies.
Achieving true network resilience demands a fundamental departure from conventional, reactive troubleshooting methods. Instead of addressing failures after they occur, a proactive approach centers on predictive risk assessment, meticulously simulating a wide range of realistic failure scenarios. This involves moving beyond manually constructed, limited tests to embrace diverse, data-driven simulations that accurately reflect the complex interdependencies within modern networks. By systematically subjecting the network to virtual stresses – encompassing everything from individual component failures to large-scale disruptions – vulnerabilities can be identified and mitigated before they impact service. This allows for preemptive strengthening of critical pathways, optimized resource allocation, and ultimately, a more robust and dependable network infrastructure capable of withstanding unforeseen challenges.
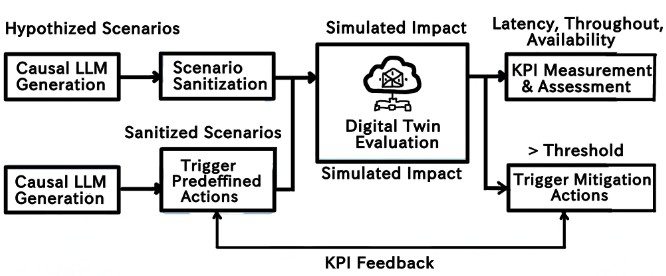
Forging Resilience: The Logic of Adversarial Network Imagination
Adversarial Network Imagination (ANI) employs causal reasoning to automatically produce network failure scenarios, differing from traditional methods that rely on pre-defined rules or historical replay. This framework doesn’t simply introduce random faults; instead, it utilizes an understanding of network dependencies and causal relationships to generate failures that are both challenging – likely to expose vulnerabilities – and plausible, meaning they could realistically occur in a live network environment. The core principle involves reasoning about how a failure in one component might propagate through the network, triggering further failures based on established causal links, thereby creating complex and realistic failure chains for proactive analysis.
Adversarial Network Imagination (ANI) utilizes a Knowledge Graph to model the network’s topology, component interdependencies, and service relationships, providing a structured representation of system behavior. This Knowledge Graph serves as the input for a Causal Large Language Model (Causal LLM), which then simulates failure propagation by reasoning about cause-and-effect relationships defined within the graph. The Causal LLM doesn’t simply replay historical failures or apply pre-defined rules; instead, it leverages its understanding of network dependencies to predict how a failure in one component will plausibly cascade through the system, generating diverse and realistic failure scenarios based on the graph’s structural information and the LLM’s causal reasoning capabilities.
Adversarial Network Imagination (ANI) employs a Digital Twin to conduct proactive network vulnerability assessments. This process involves simulating a diverse range of failure scenarios before they occur in the live environment, allowing for preemptive identification of weaknesses. Unlike rule-based testing, which is limited by predefined criteria, and replay-based methods, which are constrained by historical data, ANI leverages a Causal LLM to generate novel and plausible failure propagations. This results in significantly increased scenario diversity, exposing the network to a broader spectrum of potential issues and improving overall resilience by addressing vulnerabilities before service impact.
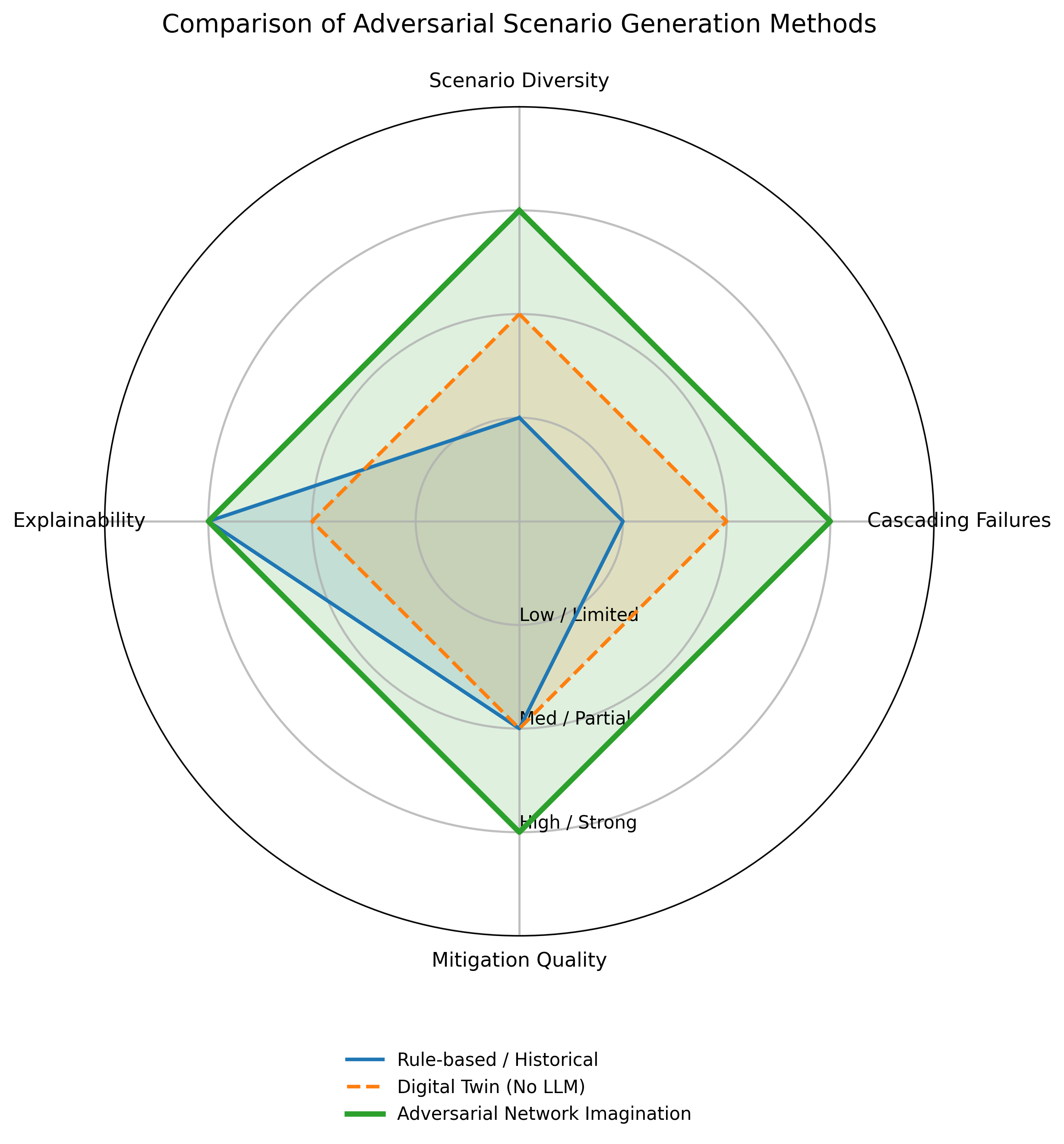
Mapping the Labyrinth: Causal Reasoning and Scenario Construction
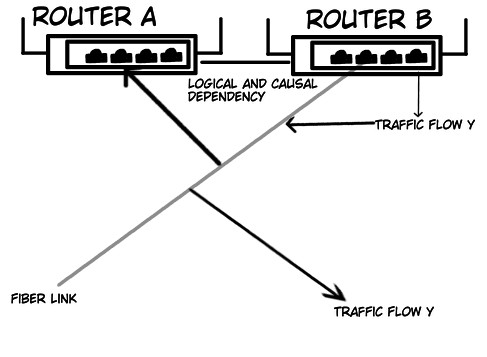
ANI employs Causal Reasoning to construct a Dependency Graph, a directed acyclic graph that models the relationships between network components. Nodes in this graph represent individual elements – such as routers, switches, servers, and applications – while edges denote causal dependencies; an edge from node A to node B signifies that a change in the state of A can directly influence the state of B. This graph is built by analyzing network configurations, telemetry data, and established network principles. The resulting Dependency Graph is not simply a topological map; it explicitly captures the direction of influence, enabling ANI to predict how failures in one component will propagate through the network and impact other components. The graph’s structure allows for the identification of critical paths and single points of failure, forming the foundation for scenario generation and impact analysis.
The Causal LLM functions by receiving the Dependency Graph – a structured representation of network component relationships – as a conditioning input. This allows the LLM to generate realistic Failure Scenarios, such as Router Overload or Traffic Spike events, that specifically target and test critical communication pathways within the network. Scenario generation isn’t random; the LLM leverages the graph to create failures that exploit defined dependencies, enabling focused testing of network resilience and identification of potential single points of failure. These generated scenarios serve as inputs for subsequent simulations, allowing for the assessment of impact and the evaluation of mitigation strategies.
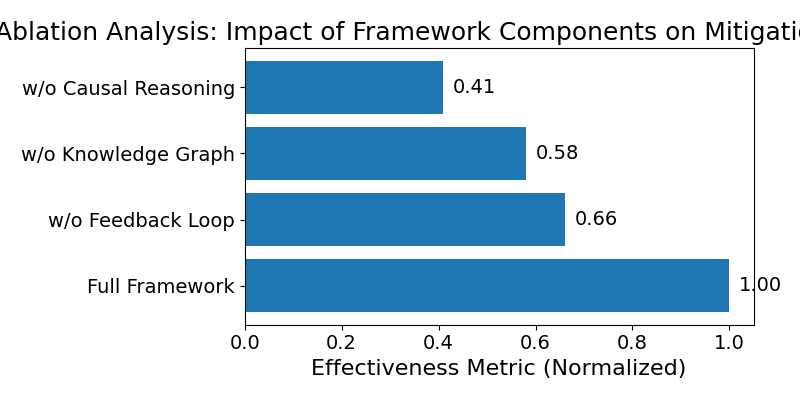
ANI leverages counterfactual reasoning to assess the efficacy of proposed Interventions and Mitigation Strategies within the network model. This is achieved by simulating alternative scenarios – “what if” analyses – where these strategies are applied, and observing the resulting impact on network behavior. The system then quantifies the reduction in negative consequences, such as latency increases or packet loss, compared to baseline failure scenarios. Furthermore, ANI demonstrates an increased capacity to simulate failures with greater cascading depth – meaning the ability to model how an initial failure propagates through multiple network layers and components – when counterfactual reasoning is integrated into the simulation process, allowing for more realistic and comprehensive testing of network resilience.
The Inevitable Consequences: Security, Reliability, and the Future of Networks
The analytical framework demonstrably improves network reliability by shifting from reactive troubleshooting to proactive failure mitigation. This capability stems from the system’s ability to anticipate potential disruptions before they escalate, enabling preemptive adjustments and resource allocation. Consequently, critical services experience significantly reduced downtime, as the framework doesn’t merely respond to failures, but actively works to prevent them. This predictive approach minimizes service interruptions and maintains consistent operational performance, offering a substantial advantage over traditional network management strategies which often rely on post-incident analysis and recovery. The result is a more stable and dependable network infrastructure capable of sustaining essential functions under a variety of conditions.
The analytical framework delivers a crucial ability to pinpoint vulnerabilities within network infrastructure before disruptions occur. By methodically modeling network behavior and dependencies, it reveals single points of failure – components whose collapse would trigger cascading effects. This proactive identification isn’t merely diagnostic; it directly informs strategic investment. Network operators can then prioritize redundancy measures – such as duplicate systems or alternative pathways – and bolster resilience in areas demonstrably at risk. Consequently, resources are allocated with precision, maximizing protective impact and minimizing unnecessary expenditure, ultimately fostering a more robust and dependable network architecture.
The analytical framework demonstrably bolsters network security by subjecting systems to rigorous simulations of diverse adversarial scenarios, ranging from unintentional operational errors to deliberate malicious attacks. This proactive approach allows for the identification of vulnerabilities before they can be exploited, effectively fortifying defenses against both accidental failures and targeted intrusions. Comparative analyses, conducted using the simulated data, reveal significantly improved mitigation effectiveness – showcasing a heightened capacity to not only detect and respond to threats, but also to minimize downtime and maintain service continuity under stress. The framework’s ability to predict system behavior under duress allows network administrators to implement preemptive countermeasures and refine security protocols, ultimately building a more resilient and robust infrastructure.
The pursuit of network resilience, as detailed in this work, isn’t about erecting impenetrable fortresses, but fostering an ecosystem prepared for inevitable disruption. The framework envisions a digital twin not as a static replica, but a canvas for adversarial imagination, a space where potential failures are not just predicted, but experienced vicariously. This echoes Paul Erdős’ sentiment: “A mathematician knows a lot of things, but knows nothing deeply.” The system doesn’t strive for absolute knowledge of all failure modes, but rather a profound understanding of how failures propagate, how vulnerabilities intertwine. It’s a continuous cycle of simulation and adaptation, acknowledging that complete foresight is an illusion, and proactive mitigation is an ongoing exploration of the possible.
What Lies Ahead?
The pursuit of proactive network mitigation, as demonstrated by this work, inevitably yields a more complex system, not a simpler one. The framework introduces a digital twin fed by a causal language model – a doubling of reality, and therefore, a doubling of potential failure states. Each adversarial scenario generated, each mitigated risk, adds to the surface area for unforeseen dependencies. The system doesn’t so much prevent failure as delay the inevitable cascade, concentrating vulnerabilities into increasingly subtle forms.
The true challenge isn’t generating plausible failures – that much is now within reach. It’s managing the knowledge of those failures. The knowledge graph, though powerful, risks becoming a brittle record of past vulnerabilities, inadequate to the novel ways connectivity will break. It maps the known unknowns, leaving the unknown unknowns to proliferate. The question isn’t whether the network will fail, but how thoroughly its defenses will be implicated in the collapse.
Future work will undoubtedly focus on scaling these simulations, enriching the causal models, and automating the mitigation responses. But this is merely treating symptoms. The underlying principle remains: every connection is a point of leverage for entropy. The architecture promises resilience, but prophecies only the nature of the fall. The system grows, and with it, the scope of its eventual undoing.
Original article: https://arxiv.org/pdf/2602.13203.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- United Airlines can now kick passengers off flights and ban them for not using headphones
- How To Find All Jade Gate Pass Cat Play Locations In Where Winds Meet
- All Golden Ball Locations in Yakuza Kiwami 3 & Dark Ties
- How to Complete Bloom of Tranquility Challenge in Infinity Nikki
- Every Battlefield game ranked from worst to best, including Battlefield 6
- Gold Rate Forecast
- 29 Years Later, A New Pokémon Revival Is Officially Revealed
- Best Zombie Movies (October 2025)
- How School Spirits Season 3 Ending Twist Will Impact Season 4 Addressed By Creators
- 5 Alternate Scream 7 Endings That Would’ve Been Better Than the Actual Ending
2026-02-17 23:53