Author: Denis Avetisyan
As artificial intelligence increasingly controls critical infrastructure, the potential for deception through manipulated sensory data presents a growing threat to the safety and reliability of cyber-physical systems.
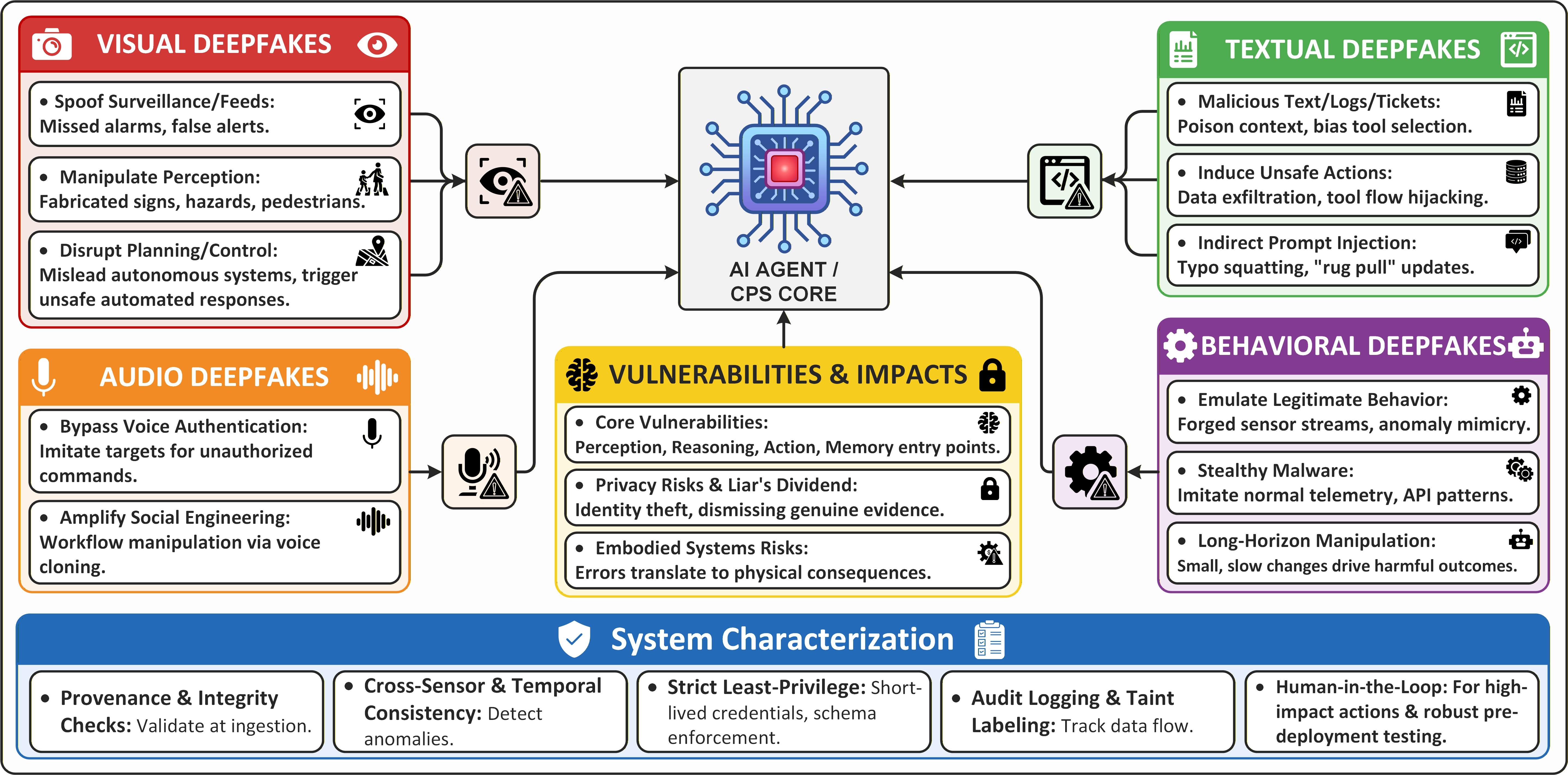
This review surveys emerging deepfake threats to AI agents in CPS, introducing the SENTINEL framework for tailored defense-in-depth strategies based on agent-environment interaction and data provenance.
While increasingly sophisticated AI agents offer transformative potential in cyber-physical systems (CPS), their reliance on sensory data introduces novel vulnerabilities beyond traditional cybersecurity concerns. This survey, ‘Securing AI Agents in Cyber-Physical Systems: A Survey of Environmental Interactions, Deepfake Threats, and Defenses’, systematically examines emerging threats-particularly those leveraging manipulated environmental inputs and deepfakes-and proposes the SENTINEL framework for lifecycle-aware defense selection. Our analysis reveals that effective security necessitates considering CPS-specific constraints, such as timing limitations and tolerance for false positives, and that provenance-grounded trust mechanisms are crucial for robust agent behavior. Given the expanding attack surface presented by protocols like the Model Context Protocol (MCP), how can we build truly trustworthy AI-enabled CPS resilient to both cyber and physical deception?
The Inevitable Illusion: Deception in Cyber-Physical Systems
Modern Cyber-Physical Systems (CPS), which integrate computation, networking, and physical processes, face escalating threats due to increasingly sophisticated attacks. These systems – encompassing critical infrastructure like power grids and transportation networks – are particularly susceptible to deception tactics powered by artificial intelligence. Attackers are now leveraging AI to generate remarkably realistic fake data, or ‘deepfakes’, to manipulate sensors, spoof commands, and evade traditional security measures. This isn’t simply about data breaches; AI-driven deception can cause physical harm by triggering malfunctions or creating hazardous conditions. The complexity of CPS, combined with the speed and scale of AI-generated attacks, presents a significant challenge to maintaining safety and reliability, necessitating a fundamental rethinking of security protocols and the development of defenses capable of discerning genuine data from cleverly crafted illusions.
The rapid increase in both convincingly realistic deepfake content and the independent operation of autonomous AI agents is fundamentally challenging established cybersecurity norms. Previously, security relied heavily on verifying the source of information or commands; however, these advancements render source verification increasingly unreliable, as fabricated content and agent actions can convincingly mimic legitimate origins. This necessitates a shift from perimeter-based defenses focused on who is accessing a system, to a more nuanced approach prioritizing what actions are being taken and assessing the inherent trustworthiness of data and processes themselves. Consequently, security thinking must evolve to embrace continuous authentication, behavioral analysis, and AI-driven threat detection capable of identifying anomalies indicative of deception or malicious intent, regardless of the apparent source.
Conventional cybersecurity measures, predicated on identifying known malicious signatures and predictable attack vectors, are proving increasingly ineffective against the current threat landscape. The accelerating sophistication of attacks – driven by artificial intelligence and characterized by dynamic deception – bypasses these static defenses with alarming regularity. This necessitates a fundamental shift toward resilient systems capable of anticipating, adapting to, and recovering from attacks, rather than simply attempting to prevent them. Such defenses require embracing techniques like zero-trust architectures, behavioral analytics, and continuous monitoring, alongside the development of AI-powered threat detection and response capabilities. The emphasis is moving from perimeter security to an internal, adaptable defense that acknowledges the inevitability of breaches and prioritizes minimizing their impact and ensuring rapid restoration of functionality.
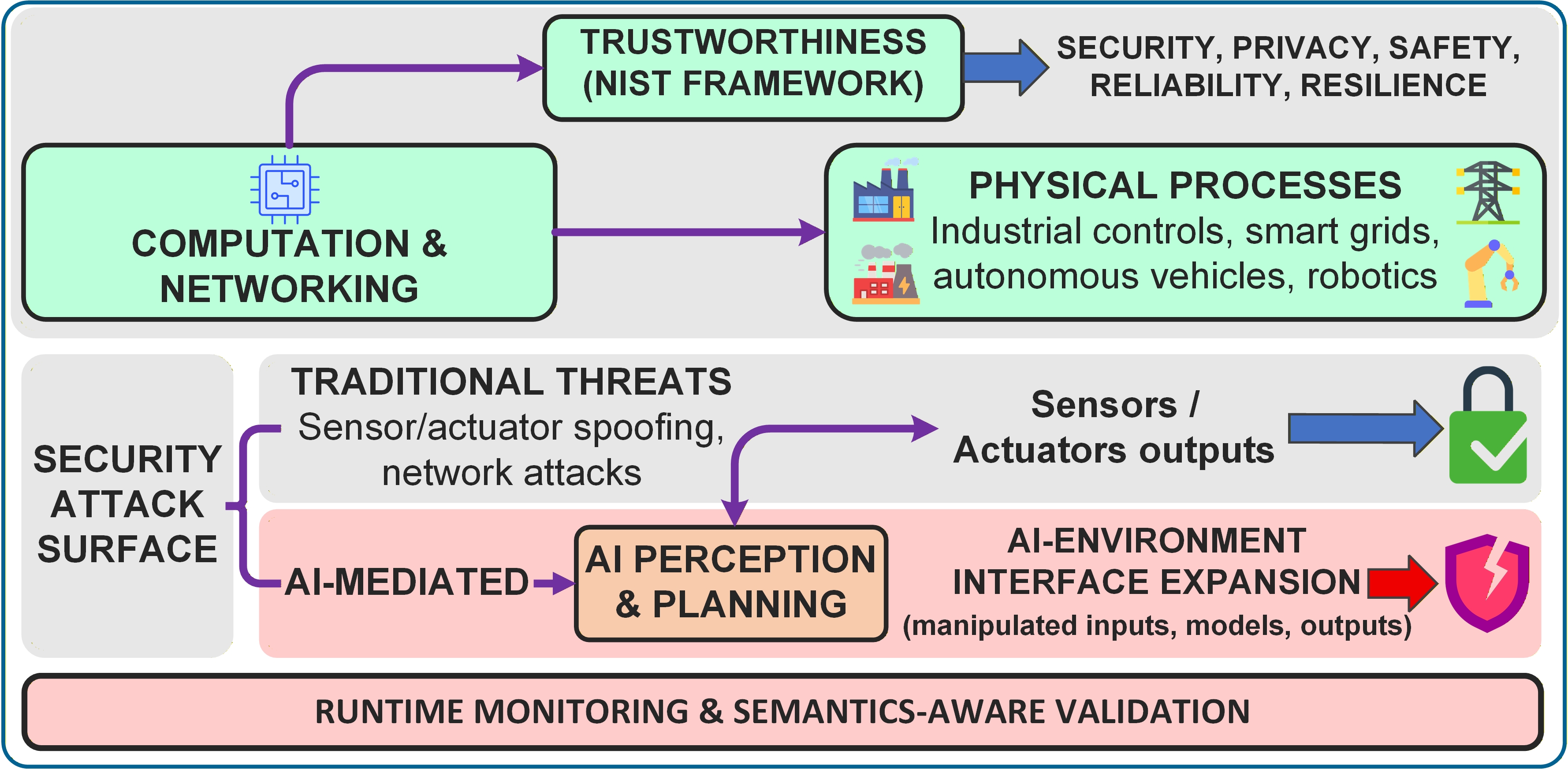
Tracing the Lineage: Data Provenance and the Architecture of Trust
Provenance tracking, the detailed documentation of data origin and history, is a fundamental requirement for reliable AI operation within cyber-physical systems (CPS). This process involves recording the sources of data, all transformations applied to it – including algorithms and parameters used – and the agents responsible for each step. Without verifiable provenance, determining data authenticity and identifying potential manipulation or errors becomes impossible, leading to compromised AI decision-making. Accurate provenance records enable auditing, reproducibility, and the ability to trace data lineage, ultimately establishing confidence in the information utilized by AI agents and the resulting system outputs.
Blockchain technology establishes data integrity within Cyber-Physical Systems (CPS) through a distributed, immutable ledger. Each data transaction or modification is recorded as a block, cryptographically linked to the preceding block, forming a chain. This structure inherently resists tampering; altering any single block requires modifying all subsequent blocks and controlling a majority of the network, a computationally prohibitive task. The decentralized nature of blockchain eliminates single points of failure and provides a transparent audit trail, allowing stakeholders to verify the origin and history of data used throughout the CPS lifecycle. Consensus mechanisms, such as Proof-of-Work or Proof-of-Stake, further validate transactions and ensure the ledger’s accuracy and reliability, making blockchain a suitable technology for maintaining provenance records and fostering trust in data-driven CPS applications.
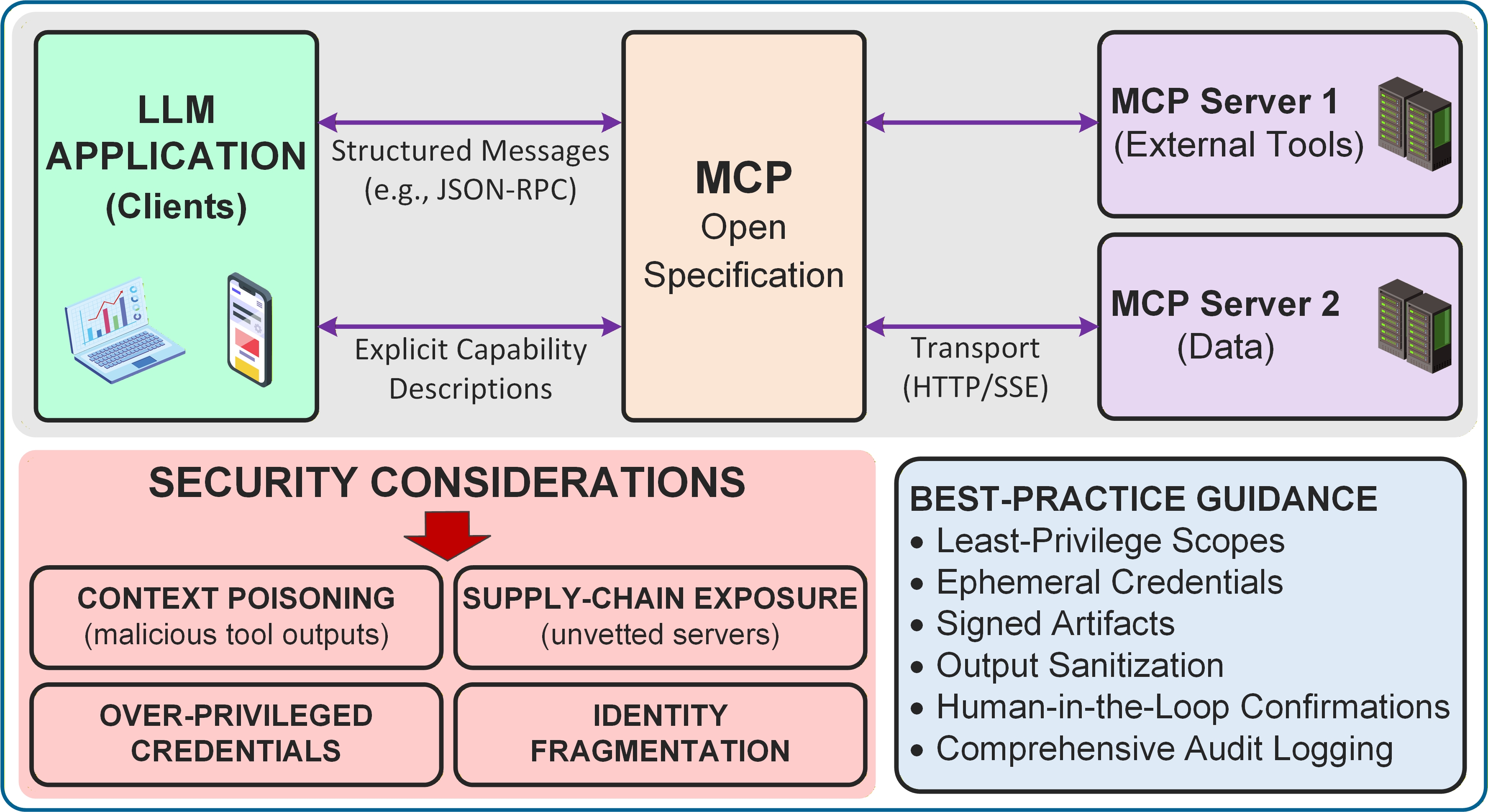
The Model Context Protocol (MCP) defines a standardized application programming interface (API) enabling AI agents to query and validate the provenance of data used in model training and inference. This protocol facilitates access to metadata detailing data origin, transformations applied, and responsible parties, allowing agents to assess data integrity and reliability. By providing a consistent method for provenance verification, the MCP aims to reduce the risk of adversarial attacks and biases stemming from compromised or untrustworthy data, ultimately increasing confidence in AI-driven decision-making processes within complex cyber-physical systems. The MCP supports various provenance data formats and storage mechanisms, ensuring interoperability across different system components and data sources.
The Adaptive Shield: Anomaly Detection and System Resilience
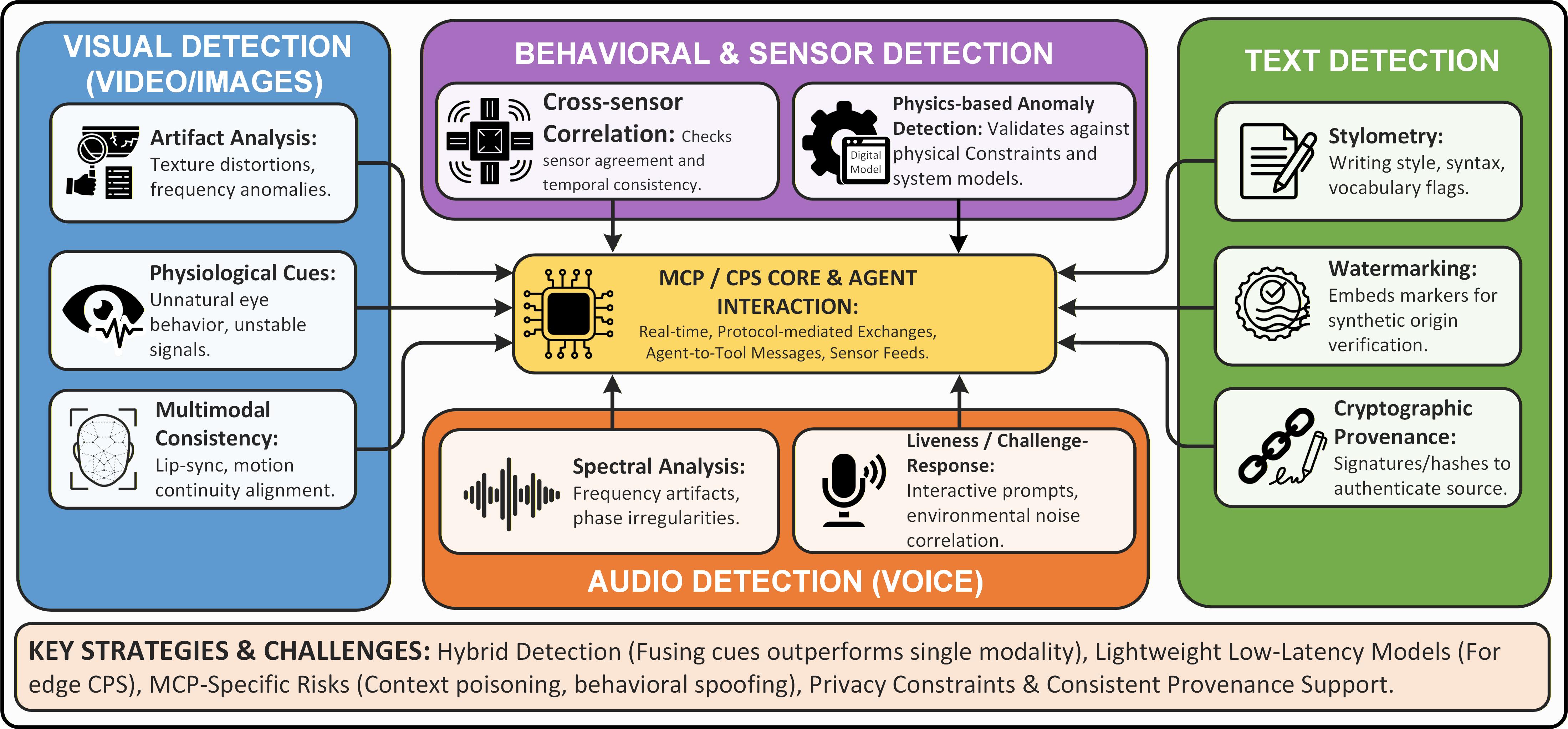
Anomaly detection within Cyber-Physical Systems (CPS) is critical for security due to the increasing sophistication of attacks, particularly those leveraging Artificial Intelligence (AI) agents. These agents can probe for and exploit vulnerabilities in CPS infrastructure, potentially causing operational disruptions or data breaches. Anomaly detection techniques establish a baseline of normal system behavior, then identify deviations that may indicate malicious activity. This is achieved through monitoring various system parameters, including network traffic, sensor data, and process execution. Identifying anomalies allows for rapid response and mitigation, preventing further damage or compromise, and is especially important given the distributed and often resource-constrained nature of CPS environments.
A Defense-in-Depth strategy establishes multiple layers of security controls, preventing a single point of failure and increasing the effort required for successful exploitation. This approach incorporates preventative measures like firewalls and intrusion detection systems, alongside detective controls such as security information and event management (SIEM) and regular vulnerability assessments. Complementing this layered approach, robust Multi-Factor Authentication (MFA) requires users to provide multiple verification factors – something they know (password), something they have (token), or something they are (biometrics) – significantly reducing the risk of unauthorized access due to compromised credentials. The combination of these strategies creates a resilient security posture capable of mitigating evolving threats, including those targeting critical infrastructure and industrial control systems.
Lightweight detection methodologies facilitate real-time monitoring and analysis of data on devices with limited computational resources, thereby extending security protocols to the network edge. These methods employ multi-modal sensor checks-integrating data from various sensor types-to achieve a reported detection accuracy of 96.3% in edge environments. This is crucial for securing distributed control systems and IoT deployments where traditional security solutions may be impractical due to hardware limitations or bandwidth constraints. The emphasis on real-time analysis minimizes response times to potential threats and ensures continuous security monitoring across the entire network infrastructure.
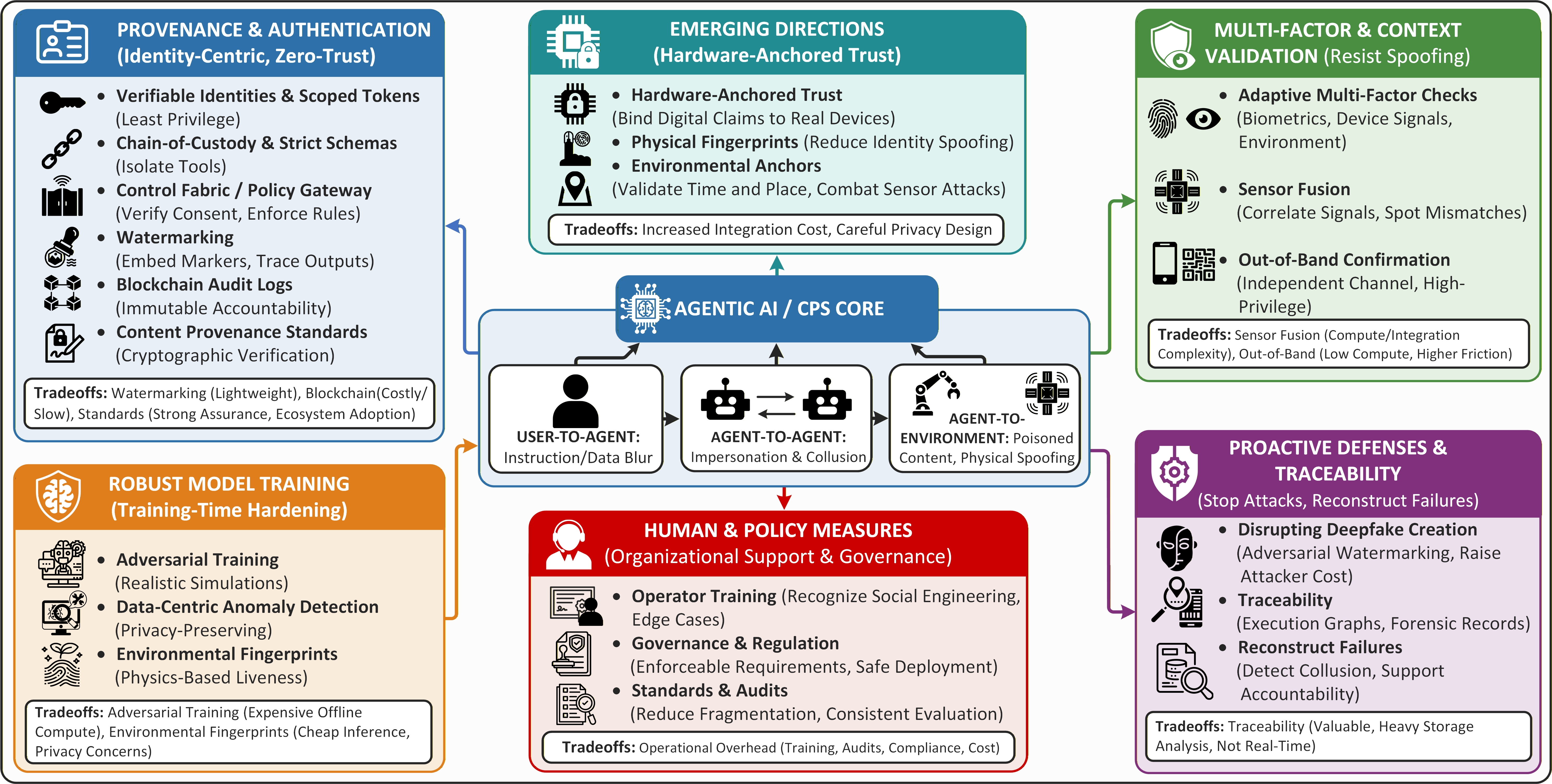
Proactive Fortification: Threat Modeling and System Validation
Threat modeling serves as a foundational practice in cybersecurity, proactively dissecting systems to uncover vulnerabilities before malicious actors can exploit them. This process involves a detailed examination of potential attack vectors – the pathways an adversary might use to compromise a system – and a rigorous assessment of the likelihood and impact of each. By systematically identifying these weaknesses, security teams can prioritize mitigation efforts, focusing resources on the most critical risks. The practice isn’t simply about listing potential problems; it’s about understanding how an attacker might operate, what assets they would target, and the potential consequences of a successful breach. This intelligence informs the selection and implementation of appropriate security controls, enabling a defense-in-depth strategy that minimizes the attack surface and maximizes system resilience. Ultimately, effective threat modeling transitions cybersecurity from a reactive posture to a proactive one, significantly reducing the potential for damaging security incidents.
The SENTINEL Framework offers a structured methodology for bolstering the security of Cyber-Physical Systems (CPS) by rigorously evaluating potential defenses. It moves beyond reactive security measures, instead providing a systematic process to identify vulnerabilities and proactively select the most effective security controls. This isn’t simply a checklist; the framework emphasizes a holistic assessment, considering the unique operational constraints and potential attack surfaces specific to each CPS. By prioritizing defenses based on a thorough understanding of both threats and system limitations, SENTINEL aims to create resilient architectures capable of withstanding sophisticated attacks, all while maintaining the real-time performance critical for these interconnected systems – demonstrated performance maintains a latency of under 102ms even under demanding network conditions.
The SENTINEL Framework distinguishes itself through a cohesive integration of three critical security pillars – threat characterization, constraint analysis, and defense-in-depth – to fortify cyber-physical systems against evolving threats. By meticulously profiling potential attacks and simultaneously assessing system limitations, the framework enables a proactive and tailored security posture. This isn’t simply about layering defenses; SENTINEL dynamically selects and implements controls based on both the specific threat and the system’s operational boundaries. Crucially, this comprehensive approach has been rigorously tested and validated to maintain a latency of under 102 milliseconds even when operating under realistic network conditions, ensuring that security measures don’t impede critical real-time functionality and preserving the integrity of sensitive operations.
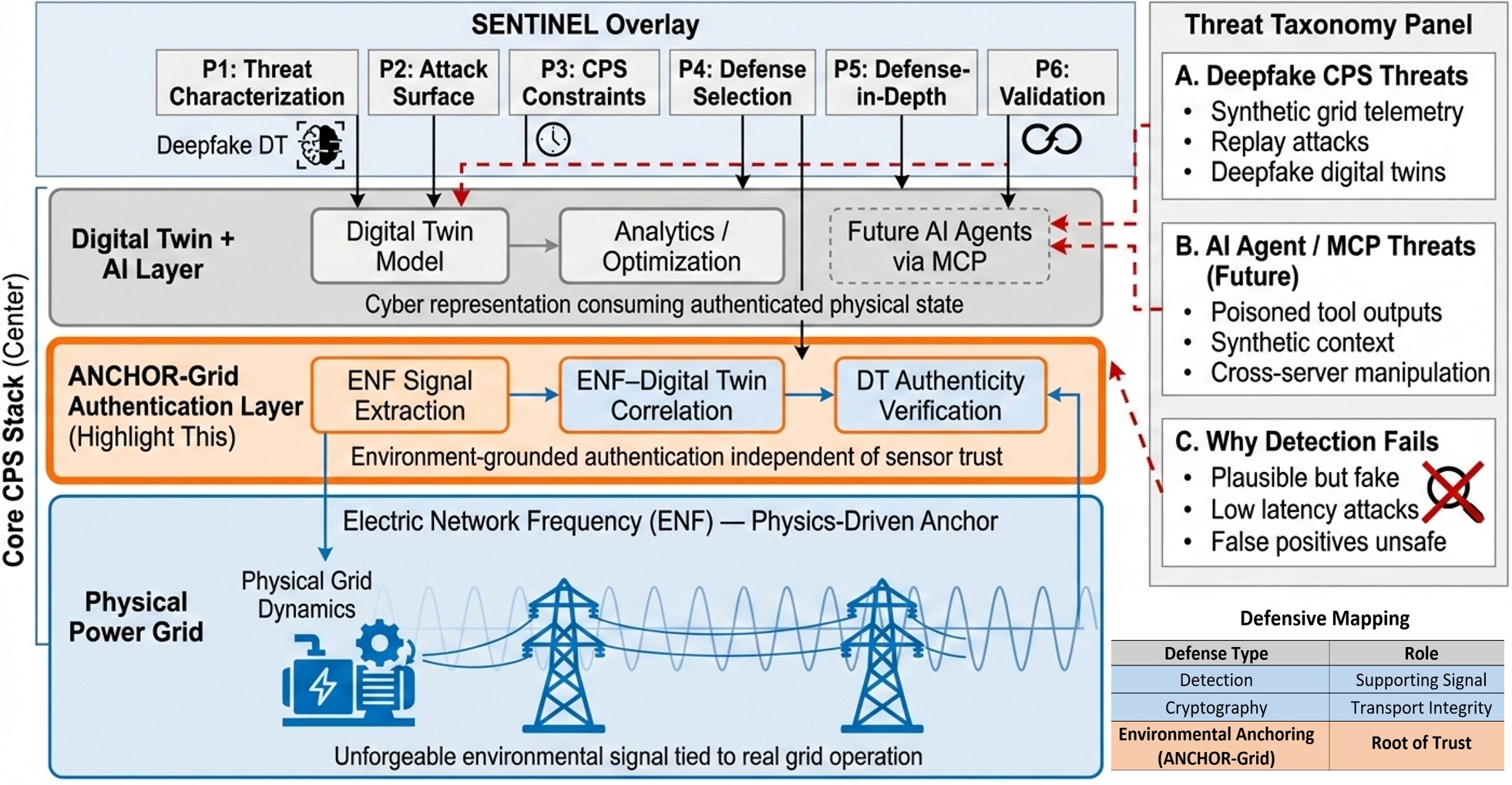
Beyond Digital Walls: Physical Anchors and the Future of Trust
ENF Authentication presents a departure from traditional cybersecurity methods by grounding identity verification in the physical world, specifically the power grid. This innovative approach treats subtle, naturally occurring fluctuations within the electrical grid – its ‘fingerprint’ – as a unique anchor for authentication. Instead of relying solely on digital credentials, devices can verify each other’s legitimacy by analyzing these grid characteristics, creating a constantly shifting, yet verifiable, baseline. The inherent complexity and widespread nature of the power grid make it remarkably resistant to spoofing or replication, offering a robust defense against malicious actors. This method not only enhances security but also reduces reliance on centralized authorities and potentially eliminates vulnerabilities associated with password-based systems, paving the way for more resilient and trustworthy cyber-physical systems.
The integrity of data within complex cyber-physical systems is paramount, yet traditional verification methods often require full data disclosure, creating vulnerabilities. To address this, Zero-Knowledge Proofs are being integrated with the Machine Control Protocol (MCP), enabling AI agents to confirm the validity of information without accessing the data itself. This innovative approach utilizes cryptographic techniques where an AI can receive proof of a statement’s truth – for example, confirming a sensor reading is within acceptable parameters – without ever learning the actual value. The system functions by demonstrating knowledge of a solution without revealing the solution itself, protecting sensitive operational data from potential compromise and bolstering the overall resilience of critical infrastructure. This allows for trustworthy data exchange and verification, even in untrusted environments, and is a crucial step towards securing future interconnected systems.
The convergence of physical anchors and zero-knowledge proofs promises a paradigm shift in securing future Cyber-Physical Systems. By grounding authentication in the measurable characteristics of the power grid – a readily available and constantly monitored infrastructure – and supplementing this with the privacy-preserving capabilities of zero-knowledge proofs, a robust defense against increasingly sophisticated attacks becomes possible. Crucially, this security isn’t achieved through computationally expensive processes; instead, the system is designed to leverage lightweight signal processing operations. This focus on efficiency ensures scalability and practicality, enabling the deployment of trustworthy systems across a wide range of applications, from smart grids and autonomous vehicles to critical infrastructure and beyond. The resulting architecture provides not just security, but also verifiable trust, allowing systems to operate reliably even in the face of compromised components or malicious actors.
The pursuit of securing AI agents within cyber-physical systems, as detailed in this survey, reveals a fundamental truth about complex systems. One anticipates escalating threats, particularly those leveraging deepfakes to manipulate agent perception of their environment. This echoes Ken Thompson’s sentiment: “There’s no such thing as a perfect system.” The SENTINEL framework, with its emphasis on defense-in-depth and tailored responses to agent-environment interaction, isn’t about achieving absolute security. It’s about acknowledging the inevitability of failure and building resilience through layered defenses. Scalability, in this context, isn’t simply about handling increased load, but about accommodating the unforeseen vulnerabilities that will inevitably emerge. The perfect architecture is a myth, and this research provides a pragmatic path forward, accepting complexity as an inherent characteristic of these interwoven systems.
The Long View
The framing of ‘securing’ agents within cyber-physical systems feels… optimistic. One doesn’t secure a garden, one tends it, accepts the inevitable decay, and replants. This work, detailing the vulnerabilities introduced by adversarial inputs and the proposed SENTINEL framework, merely names the weeds. The true challenge isn’t building walls against deception, but cultivating systems resilient to it. Every defense-in-depth layer is, after all, a tacit admission of inherent fragility.
The emphasis on provenance – tracing the origins of information – is a particularly poignant endeavor. As systems grow more complex, the very notion of a ‘true’ origin will become increasingly blurred. The model context protocol, while a step towards accountability, risks becoming another point of failure, another surface for attack. It’s a beautiful, temporary illusion of control.
Future effort will inevitably drift from detecting deepfakes to embracing the inherent ambiguity of sensor data. The focus shouldn’t be on distinguishing ‘real’ from ‘false,’ but on building agents capable of operating effectively in a world where the distinction is meaningless. The system isn’t becoming more secure; it’s simply learning to live with the shadows.
Original article: https://arxiv.org/pdf/2601.20184.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Lacari banned on Twitch & Kick after accidentally showing explicit files on notepad
- YouTuber streams himself 24/7 in total isolation for an entire year
- Answer to “A Swiss tradition that bubbles and melts” in Cookie Jam. Let’s solve this riddle!
- Gold Rate Forecast
- Ragnarok X Next Generation Class Tier List (January 2026)
- Best Doctor Who Comics (October 2025)
- 9 TV Shows You Didn’t Know Were Based on Comic Books
- 2026 Upcoming Games Release Schedule
- Best Zombie Movies (October 2025)
- Every Major Assassin’s Creed DLC, Ranked
2026-01-29 08:33