Author: Denis Avetisyan
Researchers have developed a method to predict escalating periods of high-intensity network intrusion attempts by analyzing trends in security alert streams.
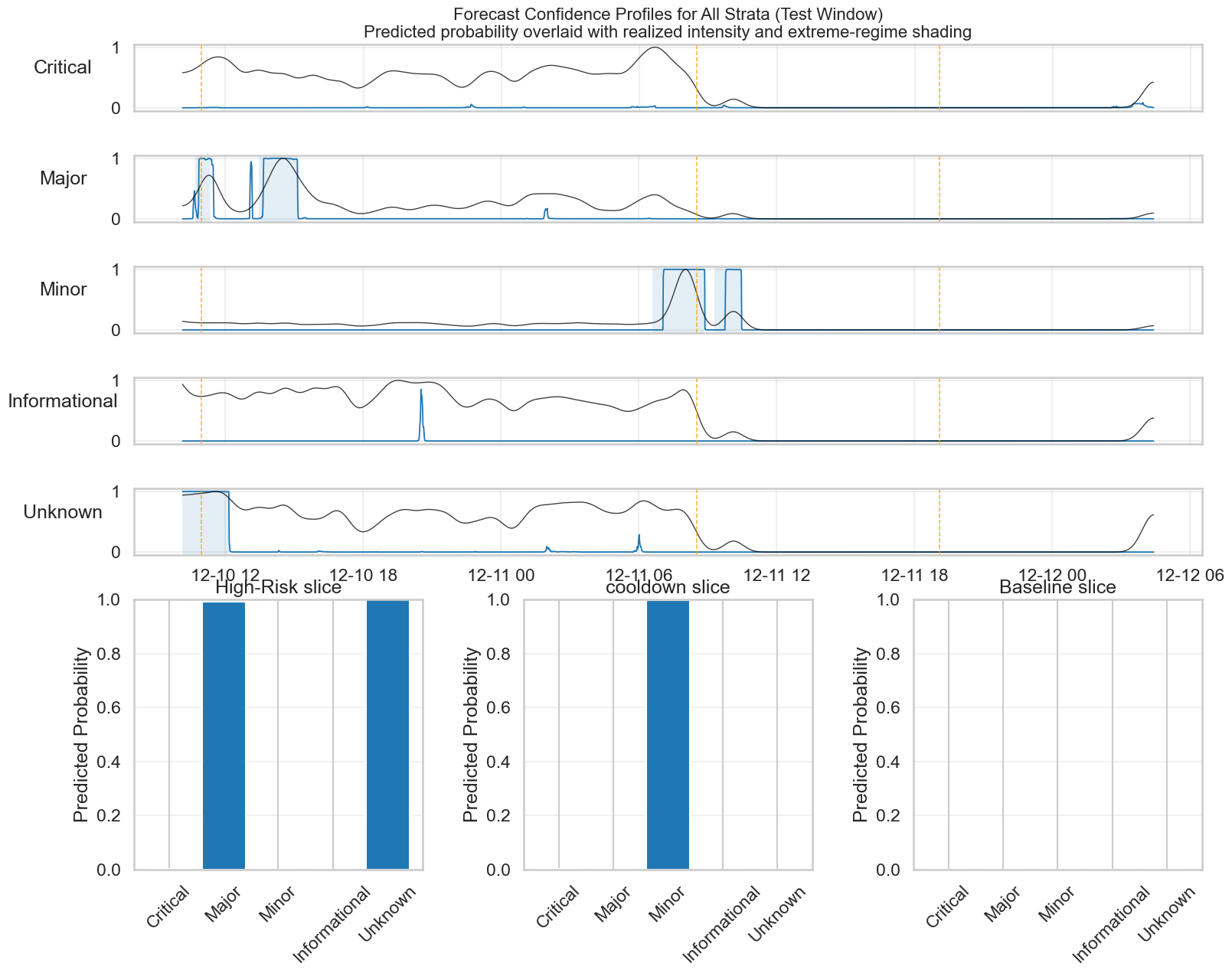
This study demonstrates that combining alert volume with temporal features like volatility and momentum accurately forecasts extreme-regime shifts in IDS alert time series.
Despite the increasing sophistication of network defenses, security operations centers remain overwhelmed by high volumes of intrusion detection system (IDS) alerts. This work, ‘Predicting Tail-Risk Escalation in IDS Alert Time Series’, addresses this challenge by applying extreme-regime forecasting-techniques borrowed from financial modeling-to characterize and predict escalating attack patterns within IDS alert streams. We demonstrate that temporal features-specifically, alert intensity combined with measures of volatility and short-term momentum-enable accurate forecasting of high-intensity attack periods, achieving up to 91% accuracy. Could these findings facilitate a shift from reactive incident response to proactive threat anticipation, ultimately enhancing cybersecurity resilience?
The Inevitable Cascade: Navigating the Rising Tide of Alerts
Contemporary network security relies heavily on intrusion detection systems, such as Suricata, which continuously monitor traffic for malicious activity. However, this vigilance comes at a cost: a relentless stream of alerts. These systems, designed to flag any potentially suspicious behavior, often generate an overwhelming volume of notifications – frequently numbering in the thousands per day for even modestly sized networks. This constant barrage presents a significant challenge for security teams, demanding considerable resources simply to process and investigate each alert. The sheer scale of the data necessitates automated tools and advanced techniques to filter out noise and prioritize genuine threats, lest critical signals be lost within the flood of information. Effectively managing this constant alert stream is no longer simply about detection, but about intelligent triage and efficient analysis.
The modern security landscape is often characterized by a relentless deluge of alerts, and this constant bombardment contributes directly to a phenomenon known as alert fatigue. Security analysts, faced with hundreds or even thousands of notifications daily, experience a gradual desensitization; the brain, overwhelmed by repetitive and often benign signals, begins to filter out potentially critical warnings. This isn’t a matter of incompetence, but a predictable consequence of cognitive overload. As the signal-to-noise ratio diminishes, the likelihood of genuine threats being overlooked increases dramatically, creating a dangerous paradox where heightened security measures inadvertently reduce effective threat detection. The result is a weakened security posture, leaving organizations vulnerable to attacks that might have been prevented with a more manageable and prioritized alert stream.
Contemporary security monitoring systems often fail to effectively distinguish between harmless network traffic and malicious activity due to the sheer volume of data they process. These systems, designed to detect anomalies, frequently trigger alerts for routine events, creating a constant barrage of notifications that obscures genuine threats. The resulting noise overwhelms security analysts, diminishing their ability to identify and respond to critical incidents. This inability to prioritize effectively stems from the limitations of signature-based detection and the increasing sophistication of attackers who employ techniques to blend malicious behavior with normal network operations. Consequently, organizations face a growing challenge in accurately assessing risk and maintaining a robust security posture amidst this relentless flood of information.
Unveiling Temporal Echoes: Characterizing Alert Dynamics
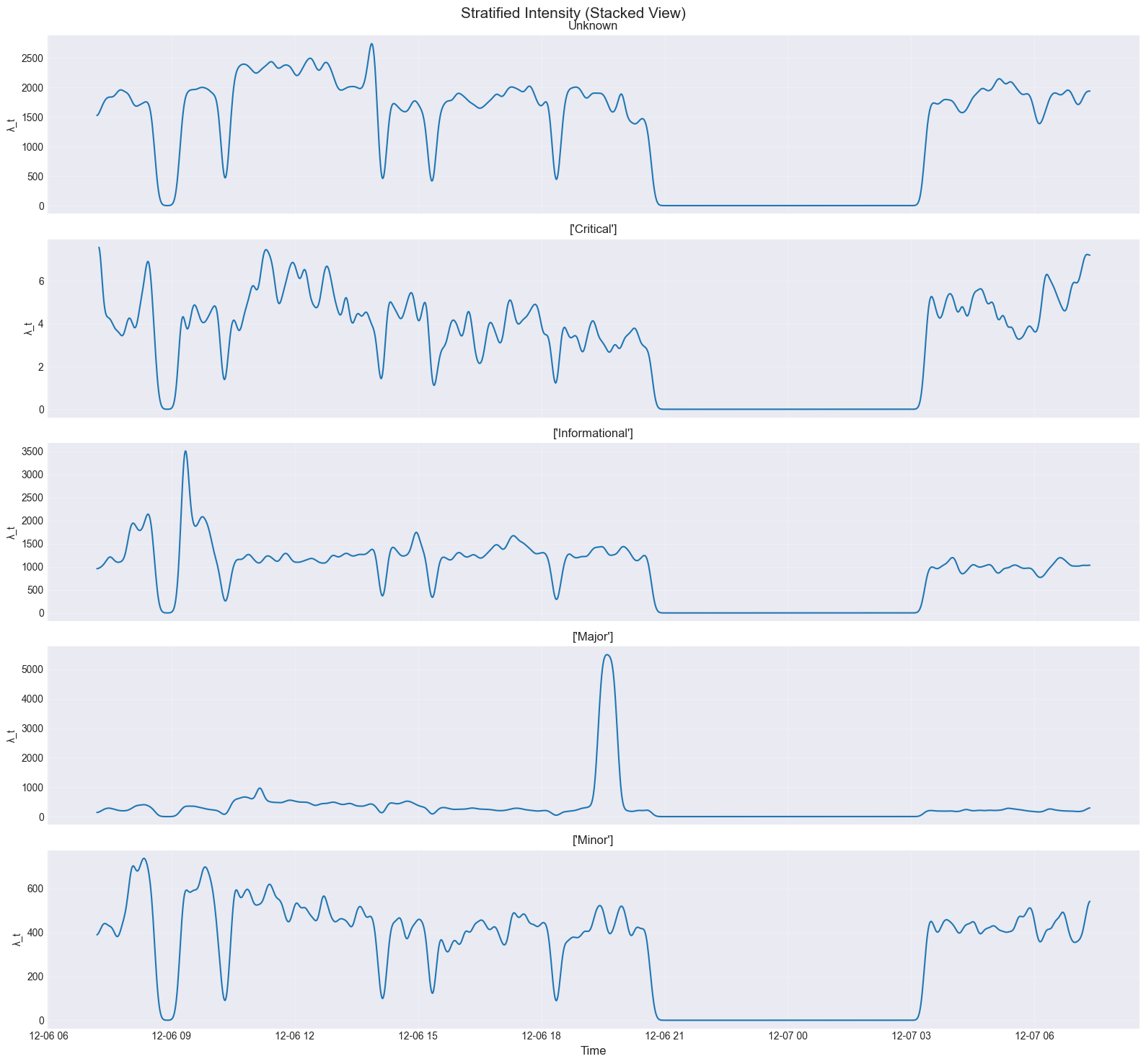
Accurate security event forecasting necessitates the analysis of Intrusion Detection System (IDS) alert streams as time series data. This approach allows for the quantification of alert arrival rates and the identification of temporal patterns indicative of underlying security dynamics. Time Series Analysis techniques, including moving averages, exponential smoothing, and autoregressive models, are applied to decompose the alert stream into constituent components – trend, seasonality, and residual noise. Examining these components reveals changes in alert frequency and distribution, providing insights into potential shifts in attacker behavior or the emergence of new threats. Furthermore, statistical measures derived from the time series, such as autocorrelation and partial autocorrelation functions, can inform the selection of appropriate forecasting models and improve prediction accuracy.
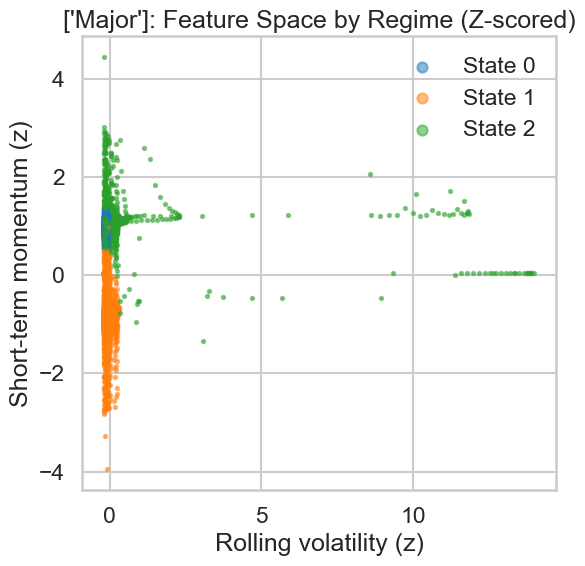
Temporal features quantify specific characteristics of Intrusion Detection System (IDS) alert streams over defined time intervals. Intensity measures the aggregate number of alerts, representing the overall rate of detected activity. Volatility calculates the standard deviation of alert counts, indicating the dispersion or irregularity of alert arrivals – higher volatility suggests unpredictable bursts of activity. Momentum tracks the change in alert intensity over time, often calculated as the difference between current and previous intensity values, revealing whether alert rates are accelerating, decelerating, or remaining stable. These features are calculated for discrete time windows, enabling the quantification of alert dynamics and facilitating predictive modeling of future activity.
The temporal features of intensity, volatility, and momentum, when applied to Intrusion Detection System (IDS) alert streams, facilitate a more granular comprehension of security events by moving beyond simple alert counts. Intensity quantifies alert arrival rates, revealing periods of heightened activity that may indicate active attacks or reconnaissance. Volatility measures the dispersion of these rates, identifying unpredictable bursts or sustained, consistent activity-potentially differentiating between automated scans and targeted intrusions. Momentum captures the rate of change in alert activity, indicating escalating or de-escalating threats. Analyzing these features collectively provides a dynamic profile of the threat landscape, allowing security analysts to prioritize investigations, refine security policies, and improve threat detection accuracy by recognizing patterns beyond static rule-based alerts.
The Illusion of Control: Predicting Extreme Regimes
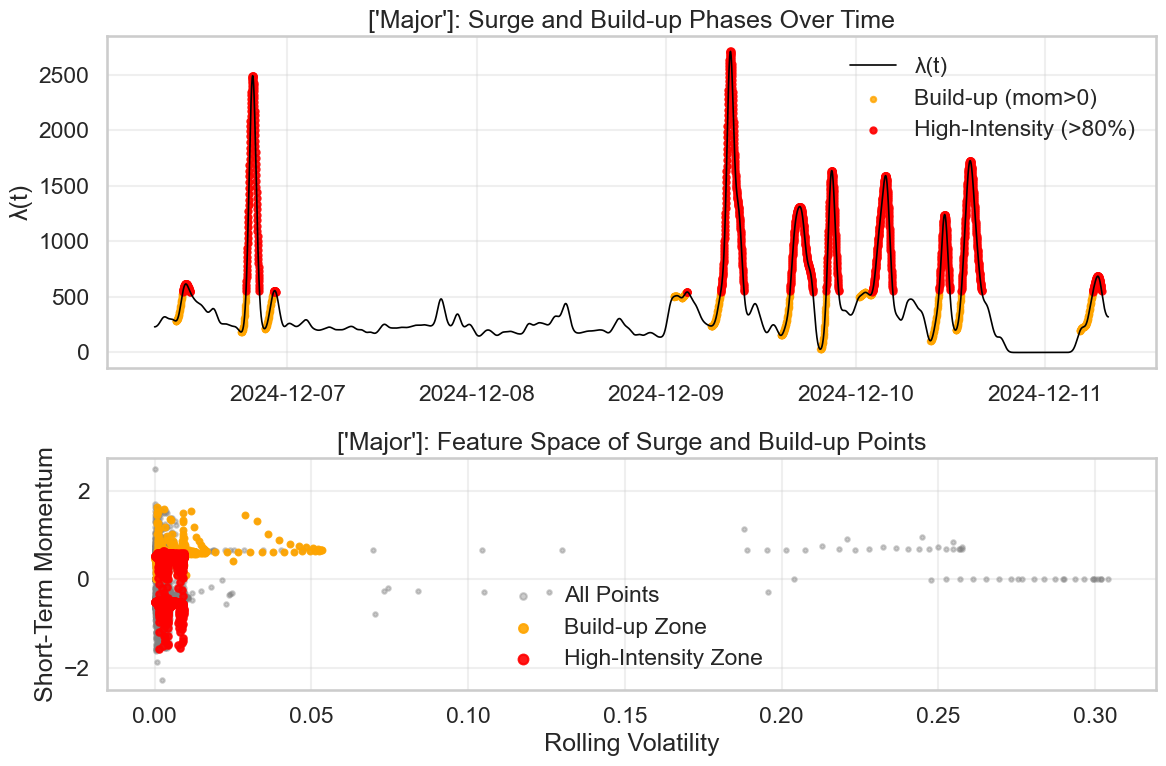
Extreme-Regime Forecasting is a predictive methodology designed to identify shifts in security alert levels towards periods of significantly heightened activity. This capability enables security teams to move beyond reactive incident response and implement proactive measures, such as increased monitoring, resource allocation, and preventative controls, before a surge in attacks materializes. The core objective is to anticipate transitions into high-intensity regimes, thereby minimizing potential damage and disruption by preparing defenses in advance of escalating threats. This differs from traditional alerting systems which typically respond to incidents as they occur, rather than forecasting their likelihood.
The forecasting approach employs machine learning algorithms, notably XGBoost, and leverages Temporal Features – data points representing time-based patterns – to predict increases in alert intensity. These Temporal Features are incorporated into the model to capture sequential dependencies and identify precursors to surges that might be missed by analyses based solely on current intensity values. The XGBoost algorithm was selected for its capacity to handle complex, non-linear relationships within the temporal data and its efficiency in identifying predictive features. Training on historical data allows the model to learn the specific patterns that consistently precede heightened alert levels, enabling proactive identification of impending surges.
The Extreme-Regime Forecasting model demonstrates a high degree of predictive capability, achieving greater than 95% accuracy when evaluated across different classifications of attack severity. This overall accuracy was determined through rigorous testing and validation procedures, confirming the model’s ability to reliably forecast periods of heightened alert intensity. Performance was consistent across strata, indicating the model isn’t biased towards detecting only specific levels of threat, and thereby supports its practical application in diverse security contexts. The consistent high accuracy validates the chosen methodology and feature engineering employed in the model’s development.
The forecasting model demonstrates a strong ability to predict transitions into extreme regimes within the Minor attack severity stratum, achieving an F1-score of 0.934 when utilizing the complete feature set. The F1-score, representing the harmonic mean of precision and recall, indicates a balanced performance in identifying both true positive and true negative instances of Minor attacks. This metric was calculated based on the model’s performance across a held-out test dataset, validating its generalization capability for this specific severity level. The complete feature set incorporates both intensity data and temporal features, suggesting that the inclusion of historical context significantly contributes to the model’s predictive power within the Minor stratum.
Analysis of the Critical stratum-representing the highest severity of attack-demonstrated a substantial performance increase when incorporating temporal features into the forecasting model. Specifically, the F1-score, a metric balancing precision and recall, improved by 97% compared to a model relying solely on attack intensity. This indicates that the timing and sequence of events leading up to a Critical-level attack are strong predictors, and that the model effectively leverages these temporal patterns to identify impending high-severity incidents with significantly improved accuracy. This improvement highlights the importance of considering historical context beyond immediate intensity levels for accurate extreme-regime forecasting.
Beyond Independence: Modeling Alert Arrival Realities
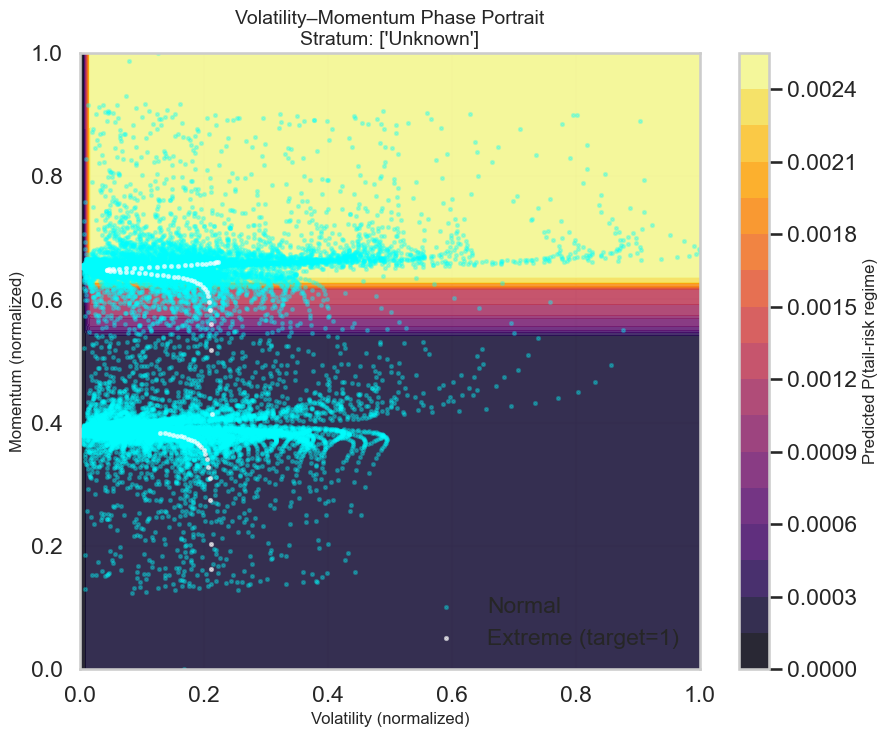
The Poisson process, commonly used to model event arrivals, assumes events occur independently at a constant average rate. However, many security events exhibit self-excitation, meaning the occurrence of one event increases the probability of subsequent events. This violates the independence assumption of the Poisson process, leading to inaccuracies when modeling phenomena like network intrusions or malware outbreaks where an initial compromise can trigger a cascade of related alerts. Specifically, the Poisson process fails to account for the temporal dependencies observed in these scenarios; it predicts a constant baseline arrival rate regardless of recent activity, unlike the clustered patterns frequently seen in real-world security data. Consequently, while serving as a useful starting point, the Poisson process often underestimates the likelihood of alert bursts and fails to capture the dynamic nature of security incidents.
The Hawkes process is a point process used to model self-exciting events, where the occurrence of one event increases the probability of future events. Unlike the Poisson process which assumes events are independent, the Hawkes process incorporates a “triggering” kernel, quantifying how much each alert influences the arrival rate of subsequent alerts. This is mathematically represented by an intensity function \lambda(t) that includes both a baseline rate and a sum of contributions from all prior events. Each prior event t_i contributes to the current intensity via a kernel g(t - t_i) , where g(t) typically decays over time, reflecting diminishing influence. The integral of this kernel determines the total excitatory effect of past events, providing a more nuanced and accurate representation of dependent alert streams than models assuming independence.
Validation of the forecasting approach relies on comparing model outputs – specifically, predictions generated by the Hawkes Process and the baseline Poisson Process – against observed historical alert data. This comparison utilizes metrics such as precision, recall, and F1-score to quantify the accuracy of each model in predicting future alert arrivals. Further refinement can be achieved by integrating Hidden Markov Models (HMM), which are capable of identifying underlying states or patterns in alert sequences, and assessing whether incorporating HMM-derived features improves forecasting performance. Rigorous statistical testing, including techniques like cross-validation, is essential to determine if the observed improvements are statistically significant and not due to random chance, thereby confirming the effectiveness of the chosen modeling techniques.
The Inevitable Shift: Mitigating Operational Risk Proactively
Predictive analysis of security alert patterns enables a shift from reactive incident handling to proactive risk mitigation. By accurately forecasting periods of heightened alert activity – termed ‘extreme alert regimes’ – security operations can dynamically allocate resources, ensuring sufficient personnel and computational power are available when demand is greatest. This preemptive approach allows for prioritization of investigations, focusing attention on genuinely critical events amidst the noise, and significantly reducing the potential for missed threats. Consequently, the organization minimizes operational risk by addressing vulnerabilities before they escalate into full-blown incidents, safeguarding both assets and reputation.
A significant benefit of proactive forecasting lies in its capacity to diminish the incidence of overlooked security incidents and simultaneously bolster the performance of security teams. By anticipating potential surges in alerts, resources can be strategically allocated, ensuring critical issues aren’t lost within a deluge of notifications. This targeted approach directly combats alert fatigue – a state of diminished responsiveness caused by constant, often irrelevant, alarms. When teams are no longer overwhelmed by excessive alerts, they can dedicate focused attention to genuine threats, leading to faster investigation times, more accurate assessments, and ultimately, a more robust security posture. The result is a system that doesn’t just generate more alerts, but meaningfully reduces risk by enabling security professionals to operate with increased clarity and efficiency.
Predictive analysis of security alerts enables a shift from reactive incident handling to proactive security management. By forecasting peaks in alert volume, systems can dynamically adjust sensitivity thresholds, temporarily suppressing low-priority notifications and focusing analyst attention on genuinely critical events. This automated triage isn’t simply about reducing noise; it facilitates informed decision-making by providing security teams with a clearer picture of emerging threats during periods of heightened activity. Consequently, organizations can implement pre-defined playbooks – automated responses to specific threat signatures – minimizing dwell time and containing potential damage before it escalates, ultimately strengthening their overall security posture and resilience.
“`html
The pursuit of forecasting within alert streams isn’t about conquering uncertainty, but acknowledging its inherent, fractal nature. This work, focused on temporal feature engineering to predict escalation in IDS alerts, understands that systems aren’t built-they become. The application of volatility and momentum as predictive signals isn’t a triumph over randomness, but a sensitive attunement to its unfolding. As Andrey Kolmogorov observed, “The most important thing in science is not to know, but to be able to predict.” This echoes throughout the paper’s exploration of high-intensity periods; the system doesn’t reveal its vulnerabilities, it portends them, and this research merely attempts to listen more closely to the whispers before they become a roar.
What Lies Ahead?
The capacity to forecast escalation in intrusion detection system alerts doesn’t diminish uncertainty; it merely redefines the boundaries of what is feared consciously. This work correctly identifies predictive signals within alert streams, but assumes a static relationship between those signals and future intensity. The true system-the network, the attackers, the defenders-is not optimized for prediction; it optimizes for adaptation. Monitoring, therefore, is not about anticipating the inevitable, but about increasing the system’s capacity to absorb surprise.
Future work must acknowledge that every feature engineered is a prophecy of its own failure. Volatility and momentum, while presently useful, will inevitably become targets for adversarial manipulation. The challenge isn’t to build more sophisticated models, but to cultivate systems that are indifferent to model accuracy. Consider, for example, the potential of incorporating deliberately ‘noisy’ data streams, designed to obscure true signals and force defenders to rely on broader, more resilient strategies.
True resilience begins where certainty ends. The next generation of intrusion detection won’t focus on predicting what will break, but on understanding how things break – and building architectures that can gracefully accommodate those failures. The objective is not a perfectly predictable system, but a beautifully fragile one.
Original article: https://arxiv.org/pdf/2601.14299.pdf
Contact the author: https://www.linkedin.com/in/avetisyan/
See also:
- Gold Rate Forecast
- Beyond Agent Alignment: Governing AI’s Collective Behavior
- Shameless is a Massive Streaming Hit 15 Years Later
- What time is Idol I Episode 9 & 10 on Netflix? K-drama release schedule
- XDC PREDICTION. XDC cryptocurrency
- Indiana Jones Franchise Future Revealed As Kathleen Kennedy Speaks Out
- Decoding Infant Cries: A New Approach to Understanding Baby’s Signals
- Stephen King Is Dominating Streaming, And It Won’t Be The Last Time In 2026
- ‘That’s A Very Bad Idea.’ One Way Chris Rock Helped SNL’s Marcello Hernández Before He Filmed His Netflix Special
- RIVER Coin’s 1,200% Surge: A Tale of Hype and Hope 🚀💸
2026-01-22 15:24